A new network of infected machines, dubbed Qbot, comprises more than half a million computers and has been used predominantly for intercepting online banking sessions with five of the largest banks in the US.
Once a system is infected, multiple pieces of malware are delivered, to make sure that the detection of one threat does not affect control over the computer, making Qbot a highly stable botnet.
The operators of the infected computers are believed to be a Russian cybercrime group.
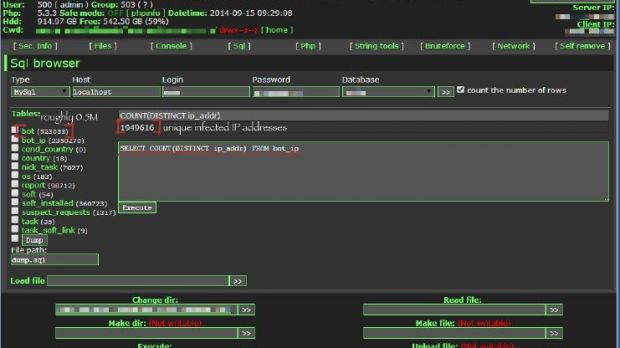
They managed to intercept the connection in the case of 800,000 encrypted online banking transactions, 59% of them related to undisclosed financial institutions in the United States.
Cybercriminals infect websites to reach PCs
Researchers at Proofpoint discovered the Qbot botnet and managed to gain access to the control panel of the network, from where they gleaned various details.
They determined that at least 520,000 computers had been enslaved based on the fact that Qbot, the initial malware dropper used by the attackers, generates a unique identifier for each infected machine.
Gaining control over this amount of systems was an elaborate scheme that involved compromising Wordpress websites.
According to Proofpoint, the malicious actors resorted to purchasing credentials for logging into shared hosting cpanel and FTP accounts.
After filtering out the non-working pairs, they logged into the legitimate websites and injected webshells acting as web-based file managers and allowing the attackers control over both their own server and the compromised one.
Visitors of the infected websites would also be served exploit kits like Sweet Orange, which would insert Qbot on the computer, increasing the botnet.
Botnet used as infrastructure for different criminal activities
With such a large network in their hands, the operators shared its potential with other cybercriminal groups, for a price.
Researchers found evidence of a module in Qbot called SocksFabric, which can create “a large tunneling network based on SOCKS5.” This could be used for transferring stolen data or for infiltrating into a company network using one of the compromised computers.
Attackers can rent SocksFabric for a period of time and conduct their nefarious activities through the Qbot network of infected machines.
The researchers say that the attackers renting time on the network can check the credits they have after logging into a control panel and selecting the desired routing of their connection, based on parameters such as country, state, city, IP address, DNS name, or bot ID.
Proofpoint draws attention to the fact that some of the compromised computers can be inside companies. “It should be noted that this service is not only used as an anonymizing service: socks within targeted organizations serve as easy infiltration points for cyber criminals,” they say.
Who are the victims?
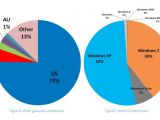
The security company says that a Russian gang is behind the entire operation and most of the Qbot victims are located in the US, accounting for 75% of the total.
Other countries seen on the distribution map with an increased number of infections include Great Britain, Canada and Italy. However, each of these accounts for less than 5% of the infections.
Most of the victims run Windows XP (52%), but a large chunk of the total (39%) use the popular Windows 7.
This shows that Microsoft still has plenty of trouble terminating the OS, despite its obvious major security issues.
 14 DAY TRIAL //
14 DAY TRIAL //