The size of the Pushdo network of infected computers is much larger than initially expected, as security firm has seen more than 76,000 machines connecting to domains under their control.
Last week, Romanian security company Bitdefender presented details about a new variant of the Pushdo malware, reporting that the fresh strain came with a changed domain generation algorithm and featured different public and private keys for the encrypted communication with the command and control (C2) server.
According to a new report from Bitdefender, received via email, the number of computers compromised by the malware has been on the rise on a constant basis, with more than 784,000 requests coming from 76,433 unique IP addresses being recorded on Monday, July 21.
These connected to domains purchased by the security company, based on the list provided by the domain generation algorithm built into Pushdo.
The data comes from Bitdefender’s sinkholing operation of the Pushdo domains. At the beginning of the process, they saw that in a time interval of less than three hours, a number of 2,336 IP addresses connected to the machines of the threat actors, waiting for instructions.
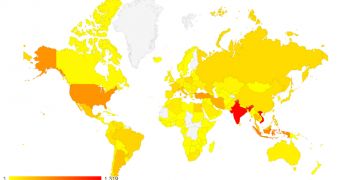
The most affected countries at that time were India, Vietnam, and Turkey, but new information reveals that the botnet is more widespread, to nations such as the United States, Argentina, Iran, Italy, Indonesia, Italy, Mexico, and Thailand.
Currently, India continues to be the region with the largest number of infected computers (8,485), followed by Vietnam (7,4930 and the United States (4,270). A a close distance is Iran, with 4,058 compromised machines.
According to Bogdan Botezatu, senior e-threat analyst at Bitdefender, the Pushdo is distributed through Upatre, a Trojan used by cybercriminals for downloading additional malware on the compromised computers.
Although there is no clear information, Pushdo may be used for funneling in Cutwail for spam distribution, scripts for conducting distributed denial-of-service (DDoS) attacks and for stealing password information.
Servers controlling the bots have been the target of multiple take-down operations from law enforcement agencies, but it seems that the malware still presents sufficient appeal to cybercriminals, who continue to use it, with slight modifications to fit their needs.
In the latest variant, security researchers have noticed that the crooks added an encrypted overlay to the binary file and “if the conditions specified in the overlay aren’t met, the sample doesn’t run properly.
Also, now the list containing approximately 100 clean domain names, which hide the hard-coded domain name of the C&C can be found here and not in the binary file,” they say in a blog post.
Although Pushdo has been on the radar of security companies and law enforcement agencies for a long time, the operators behind it seem to change, and new outbreaks are still recorded, despite various computer protection solutions being able to detect the infection.
 14 DAY TRIAL //
14 DAY TRIAL //