As good as a defensive mechanism User Account Control (UAC) is for Windows users against actions requiring administrator privileges, users can be tricked to run an app with elevated rights without raising any suspicion.
Researchers at Cylance security company developed proof-of-concept malware that can achieve this via Windows Command Prompt (cmd.exe) and the Registry Editor (regedit.exe), although the list of programs can be extended.
The focus was on these two utilities because of their importance on the system, as they are intended for running advanced administrative functions or for modify operating system settings.
User has to consent to the UAC request
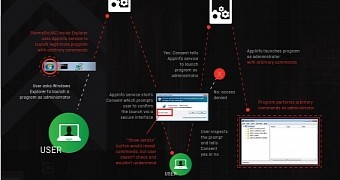
The malware created by Cylance has been dubbed ShameOnUAC, and it consists in tricking the Application Information (Appinfo) service, which is responsible for allowing programs to be launched with admin privileges, to launch software with arbitrary arguments.
Whenever a program requests elevated rights, the request is passed to Appinfo, which triggers the UAC prompt on the desktop. Users then have to explicitly allow the action to continue.
In a blog post this week, Derek Soeder explains that the procedure relies on injecting ShameOnUAC into the unprivileged explorer.exe process and hooks the AicLaunchAdminProcess targeting Command Prompt and the Registry Editor.
It then waits for the user to launch one of the two targets with administrative rights and modifies the request before it reaches the Appinfo service, adding arbitrary arguments, such as executing a command chosen by the attacker.
If the user approves the UAC message, privilege escalation is achieved by the threat actor.
Plot thickens in the case of the Registry Editor
With the registry editor, however, ShamOnUAC can increases its grip on the computer beyond administrator, to SYSTEM, used by Windows processes and services.
“Regedit's supported arguments naturally involve the registry, so ShameOnUAC causes Regedit to silently install a .reg file via a '/S' argument. If that were the extent of it, the user would never get their expected Regedit window and might wonder what happened. ShameOnUAC's solution is to cause the .reg file to register a library in AppInit_DLLs and then issue a second elevation request,” Soeder says.
He adds that the request triggers a new consent.exe process, which is executed with SYSTEM privileges and loads the ShameOnUAC library, before the user gets to see any warning. In the next step, the parameters for the alert are modified and the UAC message is completely suppressed.
There is a way to prevent such nefarious actions, though, and it relies on the user checking the details in the UAC prompt. However, this reaction is far from being part of the regular behavior when a UAC is shown.
Soeder points out that ShameOnUAC adds to the list of tricks that can be played on UAC, referencing previous work from security researcher Rob Fuller.
 14 DAY TRIAL //
14 DAY TRIAL //