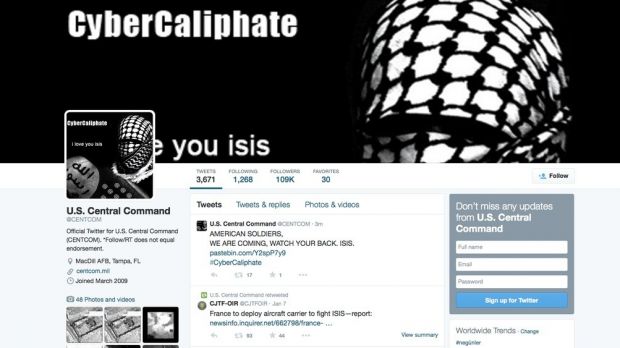
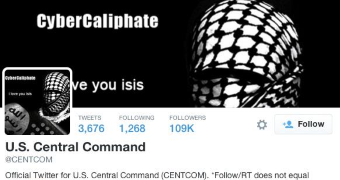
Individuals supporting the Islamic State terrorist group hijacked the Twitter and YouTube profiles of the US Central Command (CENTCOM) on Monday and posted a warning to the US soldiers.
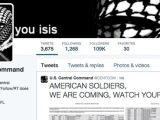
In a post on Twitter, the hackers, operating under the name CyberCaliphate, published a message that read “AMERICAN SOLDIERS, WE ARE COMING, WATCH YOUR BACK. ISIS.”
On the YouTube profile of CENTCOM, the cyber-vandalism activity carried out by the CyberCaliphate group consisted in uploading and publishing multiple videos with ISIS propaganda and militants.
Attackers linked to military documents
For a period of about 30 minutes, both social accounts were under the control of unauthorized entities; then, they were taken offline for a temporary period of time. Currently, CENTCOM’s Twitter is under the control of its rightful owner, but the YouTube channel continues to be down.
CyberCaliphate also published links to documents containing information about retired US Army generals and about military plans in sensitive regions across the globe, such as China, North Korea, Africa, Indonesia, and the Caspian area.
This fueled the speculation and fear that the US military computer system had been compromised and classified information had been extracted.
Despite CyberCaliphate’s attempts to pass this data as being secret to the public and its claims that it was obtained through compromising US military computers, CENTCOM says in an official statement that the servers of the Defense Department have not been breached on account of this incident and that its operations remained unaffected.
“CENTCOM's operational military networks were not compromised and there was no operational impact to U.S. Central Command,” the official release reads.
Incident is a PR blow against US military
Hijacking social media accounts is not uncommon, even in the case of big corporations and organizations. It all boils down to the fact that the profiles are handled by an individual that can be tricked into disclosing the credentials to an attacker, if adequate social engineering skills are at work.
As it happens with all targeted attacks, certain preparation is required though, to make the compromise operation successful. The hijackers have likely relied on spear-phishing to gain access to the email account of the person responsible with social media; if the two-factor authentication (2FA) security measure was not enabled, then changing the log-in credentials would be a cinch.
However, this time pro-ISIS perpetrators hit the accounts of a terrorism-fighting military organization, and embarrassing CENTCOM this way makes for perfect propaganda for ISIS, even if the “hack” itself is not sophisticated in nature.
 14 DAY TRIAL //
14 DAY TRIAL //