Vulnerability Lab researchers have found a post inject (input validation) web vulnerability in the 5.8.1.8 version of the SonicOS network security platform. Products from the Dell SonicWALL Network Security Appliance (NSA) series that rely on the platform had been affected before the company addressed the bug.
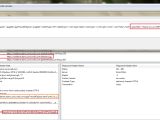
“The vulnerability allows an attacker to inject via POST request own malicious script code in the vulnerable module on application side (persistent),” the researchers explained.
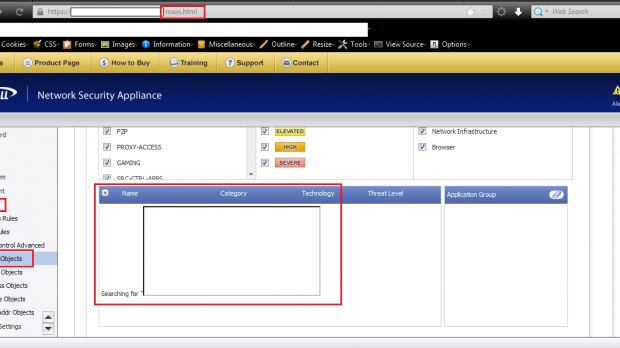
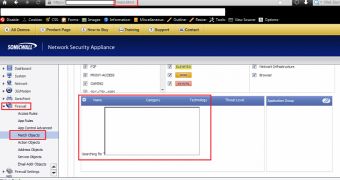
“The vulnerability is located in the Firewall > Match Object > Edit Match Object section when processing to request via the `Search > appFirewallObjects` module the bound vulnerable [searchStr] application parameter. The persistent injected script code will be executed out of the searchstr name listing web application context.”
The medium-severity security hole can be remotely exploited by an attacker with low user privileges and it doesn’t require any interaction on the victim’s part.
If exploited successfully, the vulnerability can lead to “persistent session hijacking, persistent phishing, external redirect, external malware loads and persistent vulnerable module context manipulation.”
SonicWall has been notified by the researchers on November 18 and the issue has been addressed by the company with the release of the 5.8.1.9 variant at the beginning of December. Customers are advised to install the new version.
A detailed proof-of-concept can be found here. Screenshots (see the gallery) that show the existence of the vulnerability have been provided to us by the experts.
 14 DAY TRIAL //
14 DAY TRIAL //