SSL/TLS certificate validation flaws that allow interception of sensitive user data via man-in-the-middle (MitM) attacks persist in a set of 15 popular apps in Google’s official app repository, after their authors were notified of the vulnerabilities in early September 2014.
The initial testing was carried out by the CERT division of the Software Engineering Institute at Carnegie Mellon University and revealed that more than 23,500 apps presented some sort of SSL/TLS certificate verification failure or error.
Tested apps racked up hundreds of millions of installs
Seven months later, security researcher Sam Bowne from the City College at San Francisco reiterated the test on Snap Secure, an app installed at least 100,000 times, and found that despite receiving an update post CERT’s notification, a trivial MitM attack from a third party could still get user credentials in plain text.
14 other apps were tested this way, some of them with a count of at least 100 million installs, and these were also vulnerable to the same type of attack, where the certificate for the encrypted connection was not properly validated.
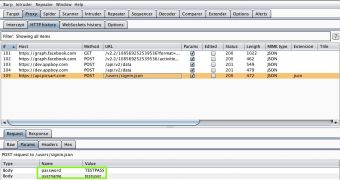
Bowne used the freely available Burp suite configured to act as a proxy between the client and the server, without a valid certificate installed. This means that the user would be alerted of fraudulent HTTPS connections and the sensitive information would not be passed to the untrusted system intercepting the traffic.
The testbed included PicsArt, ES File Explorer File Manager, Truecaller, OKCupid, Instachat, CityShop - for Craigslist, ASTRO File Manager with Cloud, and DISH Anywhere, all totaling at least 325 million installations on Android devices across the globe.
One app sends user data without encryption
In most of the cases, Bowne showed that the login account credentials could be easily extracted from the traffic to the proxy, despite the availability of an encrypted connection.
Truecaller, updated on April 21 and with over 50 million installations, did not use a secure connection at all, Bowne found, allowing the username, password and phone number to be delivered unprotected. More than this, the researcher says that this information was sent in plain text each time the user clicked the link for frequently asked questions.
With SomNote, however, the sensitive information was not accessible in plain text because it was sent to the server in hashed form, which does add some protection for the data. Nevertheless, the SSL/TLS certificate is not validated either.
Since CERT’s assessment, most of these apps received multiple updates, but it looks like none of them solved the certificate verification issue.
Bowne could not assess all the products CERT did, but it is likely that many more apps have still not fixed the initial problems and expose user data in trivial attacks.
 14 DAY TRIAL //
14 DAY TRIAL //