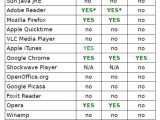
According to research from vulnerability management company Secunia, a lot of popular applications fail to make use of the defenses implemented in Windows. Applications like Java, Adobe Reader, Mozilla Firefox have broken, incomplete or missing DEP and ASLR support.
DEP (Data Execution Prevention) is a security feature first introduced in Windows XP Service Pack 2, which prevents programs from executing code stored in writable memory. The technology is aimed at preventing arbitrary code execution following the exploitation of memory corruption vulnerabilities.
However, while DEP makes it harder to exploit vulnerabilities towards this purpose, it is certainly no silver bullet and can be defeated by using a technique known as "return-into-libc." Because of this, starting with Windows Vista Microsoft introduced another defense mechanism known as ASLR (Address Space Layout Randomization).
The ASLR feature randomizes the memory address space where a PE file (.exe, .dll, .scr, .sys, .drv, .ocx) is loaded after each reboot. "If both DEP and ASLR are correctly deployed, the ease of exploit development decreases significantly, code execution being sometimes impossible to achieve in one attempt. However, note that a single module for which ASLR is not applied can at times be enough for code execution to succeed," the Secunia researchers explain.
The company's study (PDF) reveals that even though both of these technologies have existed for three years now, many of today's ubiquitous programs still have support for just one or none of them. In other cases, the existent implementations are broken because one or more .DLLs load at fixed memory addresses.
Therefore, as of June 2010, Java Runtime Environment, Apple QuickTime, VLC Media Player, OpenOffice, Google Picasa, Foxit Reader, Winamp and RealPlayer don't have neither DEP or ASLR enabled. Adobe Reader and Apple iTunes (only Win7) have DEP support, but not full ASLR.
That is also the case of Mozilla Firefox, Opera and Safari. Speaking of browsers, Chrome shows its superiority again, as far as security is concerned, with a proper implementation of DEP on both XP and Windows 7, as well as full support for ASLR.
If we look closely at Secunia's list of shame, we can easily understand why some of these programs have become the hackers' favorite targets. "While most Microsoft applications take full advantage of DEP and ASLR, third-party applications have yet to fully adapt to the requirements of the two mechanisms. If we also consider the increasing number of vulnerabilities discovered in third-party applications, an attacker's choice for targeting a popular third-party application rather than a Microsoft product becomes very understandable," the researchers conclude.
You can follow the editor on Twitter @lconstantin

 14 DAY TRIAL //
14 DAY TRIAL //