SSL vulnerabilities in Android apps offer cybercriminals the possibility to run man-in-the-middle (MiTM) attacks on users, thus intercepting communication between the client and the server.
After analyzing the most downloaded and free 1,000 apps on Google Play, security researchers at FireEye found that 674 of them included SSL vulnerabilities that could be exploited by threat actors in order to gain access to sensitive information.
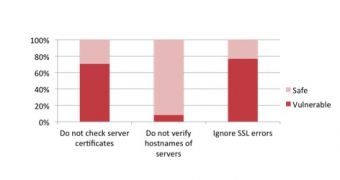
FireEye Mobile Security Team discovered that about 73% (448) of the 614 apps relying on SSL/TLS protocols for communication with a remote server had trust managers that did not run a certificate validation.
Checking to see whether there is a trusted party at the other end of the communication is essential for secure exchange of the information and in lack of a trust manager, MiTM attacks are a successful way to snoop on sensitive data.
There is the possibility that a cybercriminal uses a rogue certificate, signed by a Certificate Authority (CA), “therefore, to prevent a MITM attack, the hostname of the server extracted from the CA-issued certificate must match the hostname of the server the application intends to connect,” FireEye writes in a blog post.
Researchers found that 50 of the analyzed Android apps rely on their own hostname verifiers that fail to perform the check.
Another issue referred to ignoring SSL errors generated by Webkit and extended to as many of 219 apps out of 285 using Webkit . Any such error should be caught and mitigated in order to allow rendering of a web page through a secure connection.
The FireEye team also ran some tests on 10,000 randomly selected free apps in Google Play and observed similar problems.
“Roughly 4,000 (40%) use trust managers that do not check server certificates, exposing any data they exchange with their servers to potential theft. Furthermore, around 750 (7%) applications use hostname verifiers that do not check hostnames, implying that they are incapable of detecting redirection attacks where the attacker redirects the server request to a malicious webserver controlled by the attacker. Finally, 1,300 (13%) do not check SSL errors when they use Webkit,” they wrote.
In many cases, the vulnerabilities detected were not necessarily in the studied apps, but third-party libraries integrated in them.
The experts said that one popular ad library, Flurry, which was present in more than 9,500 apps with over 50,000 downloads used HTTPS with a vulnerable trust manager in versions earlier than 3.4; the total number of downloads for the affected apps was reported to more than 8.7 billion.
FireEye alerted the developers of the glitchy apps about the vulnerabilities and they have addressed them in the next versions released.
 14 DAY TRIAL //
14 DAY TRIAL //