A malvertising campaign discovered by researchers at Malwarebytes leverages pop-under advertisements distributed through Popcash ad network to infect computers with CryptoWall and possibly other types of malware.
Unlike regular pop-ups or ads embedded in web pages, pop-unders are more difficult to notice as they load in a separate browser tab. This particularity, however, is not relevant for infections occurring via the so called drive-by download attacks leveraged by malvertising.
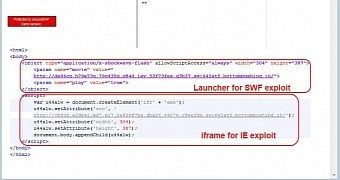
Magnitude EK exploits Flash, delivers CryptoWall via Necurs dropper
According to Jerome Segura from Malwarebytes, the cybercriminals use Magnitude web-based attack tool to deliver exploits for Internet Explorer and Flash Player (CVE-2015-3090) that funnel in a malware downloader.
Segura says that the dropper is Necurs, and it adds a variant of the infamous CryptoWall crypto-malware to the compromised system. The researcher points out that the exploit kit operator is not limited to distributing these pieces of malware and other threats can be sent to vulnerable computers.
Once again, it falls on the shoulders of the user to ensure the safety of the system, by installing the latest updates for Flash Player and Internet Explorer.
It is worth noting that Chrome and Internet Explorer (on Windows 8 and up) receive patches for Adobe’s plugin automatically. New builds of the runtime version of the software need to be updated manually, if the automatic update mechanism is not enabled.
A joint effort is necessary to prevent malvertising incidents
With CryptoWall installed on the computer, users without file backups do not stand a chance of getting their data back without paying the ransom imposed by the crooks. Segura says that the fee is set to $500 / €440, a price not many are able to pay.
“Paying the ransom as a desperate measure to get those important files can be understood but it also keeps this underground economy flourishing,” the researcher warns, echoing the long time recommendation from security experts not to pay.
Combating malvertising requires a collective effort from publishers, ad networks and visitors. Publishers carefully selecting partners, networks making sure that the code served is clean and users keeping their software products up-to-date, is the recipe for protecting against this type of risk.
 14 DAY TRIAL //
14 DAY TRIAL //