The founder and CEO of Vulnerability Lab Benjamin Kunz Mejri, with the aid of researchers Alexander Fuchs and Ucha Gobejishvili, identified a number of high risk vulnerabilities that affected Skype, the popular instant messaging application.
As the experts demonstrated, Skype 5.8.0.156 for Windows, Skype 5.5.2340 for Mac and Skype 2.2.x Beta for Linux were all affected by a pointer corruption vulnerability that has a persistent weakness vector.
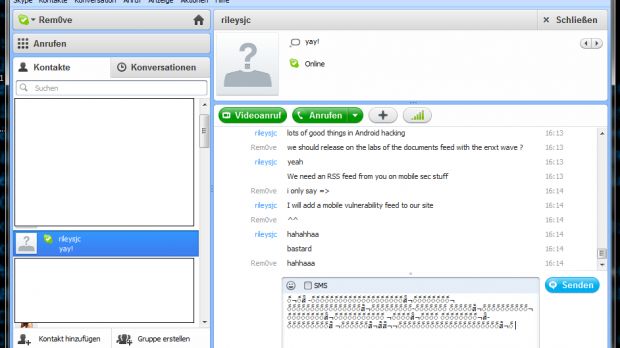
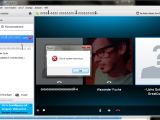
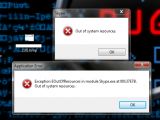
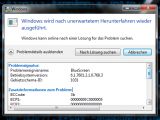
The pointer corruption vulnerability can be exploited when the application is processing specially crafted symbol messages via the chat box. An attacker could leverage this security hole to freeze, block, crash and even destroy the active communication window.
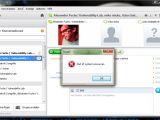
The persistent weakness vector allows a remote attacker to cause a denial of service state and a persistent error message by inserting the special symbol message into the name field of the Add a contact window.
Furthermore, the Group Topic & Group Information Name module can be exploited to cause a stable group error with different exceptions.
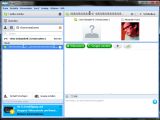
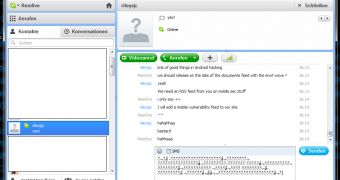
The callto function part of the Facebook integration module also presents a security hole that can be leveraged by an attacker if he uses the malicious symbol string as his nickname.
Vulnerability Lab reported the findings to Skype on February 24, and on March 5 a new version of the instant messaging application was made available to address the issues.
In order to mitigate the threats, customers are advised to update to the latest version of Skype.
Vulnerability Lab provided us with a proof of concept, screenshots and a video that demonstrate the existence of the flaws:
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile.
 14 DAY TRIAL //
14 DAY TRIAL //