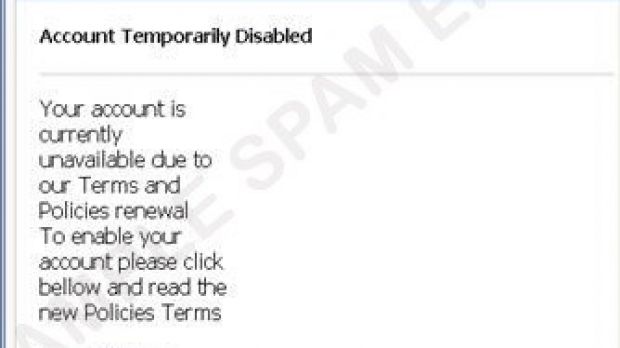
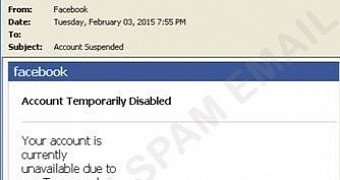
Emails purporting to be alerts regarding Google Chrome and Facebook, and pointing to CTB-Locker file-encrypting malware samples, have been found to share compromised websites used for phishing campaigns.
The messages containing a link to download Critroni, alternative name for CTB-Locker, masquerade as a notification for a new Chrome browser update or for the suspension of the Facebook account of the recipient.
All compromised websites have one IP address in common
At the beginning of the month, security researchers at Malwarebytes observed the fake notices for Google’s browser, noting that the cybercriminals relied on a dynamic redirection mechanism to hide the compromised websites.
On Wednesday, Trend Micro security company confirmed this campaign, adding that the Facebook name was leveraged to the same purpose, as part of the same campaign, although the samples they caught were different.
“Our findings show that both variants [of Critroni] are hosted in compromised sites. And interestingly enough, each variant is hosted on a group of compromised sites that is linked to one IP address,” a blog post from Michael Marcos, Trend Micro threat response engineer, informs.
After analyzing the compromised websites hosting the two malicious payloads, they made the connection to a group known to be active on the PayPal phishing scene.
Marcos explains that the fake PayPal pages served to the potential victims asked for more information than just the log-in details, including contact and credit card information. The lure is a pretense that unusual activity had been recorded for the account and that identity confirmation is required to settle the matter.
At first glance, fake email addresses look legitimate
The phishing scammers rely on email addresses that appear legitimate in order to increase their success chances. The messages are sent from [email protected], [email protected] and [email protected].
Even if they look valid, none of them is, since fb.com is used by Facebook for its corporate email domain and Pay Pal uses the .com TLD (top-level domain) for communication. In the case of Google, splitting the name of the company is a clear sign of fraud.
CTB-Locker recorded a surge in the number of infections during the month of February, researchers at F-Secure say. This may be accounted by the fact that cybercriminals released a new version of the malware recently, which increases the ransom fee to three Bitcoins ($670 / €587) and extends the payment period to 96 hours.
 14 DAY TRIAL //
14 DAY TRIAL //