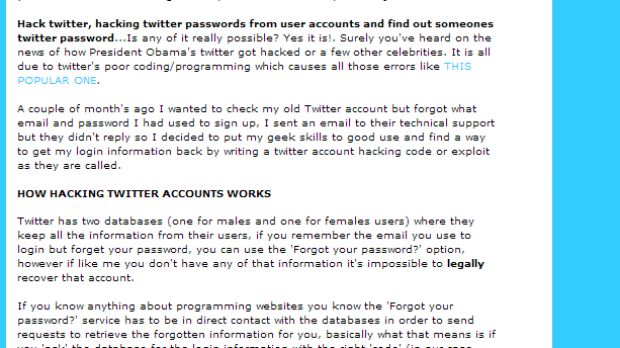
Inventive cybercriminals have started sending out emails advertising a “web based exploit” that can allegedly be utilized to hack into any Twitter account. The “offer” is part of a clever phishing scam.
There are two ways to phish out a Twitter user’s password.
One of them involves a replica of the Twitter login page. The cybercriminal must simply convince the victims that it’s real and have them enter their usernames and passwords.
The second one – analyzed by GFI Labs experts – is not as complex from a technical standpoint, but it’s much more creative.
“Do you want to learn how to hack twitter? Are you looking for a way to hack your friends twitter account without them finding out? Interested in finding out ways to hack someone’s profile? Maybe you want to take a quick peek at their direct message inbox, steal their username or find a glitch to use a hacking script,” the emails read.
They continue, “In this article I will show you a fairly easy step by step guide on how to hack twitter user accounts without having to directly hack into twitter or their computer and risk getting caught.”
After a fairly long story in which potential victims are told all about the inner workings of Twitter and how apparently users are split up into separate databases based on their gender, the fun begins.
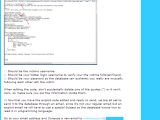
A piece of code, which allegedly represents part of the exploit, is presented to users. In order for the hack to work, they must replace certain parameters with the victim’s username, their own username (to verify if the target is a follower), and their own password, and send them via email to a fake twitter support address.
The user’s own password is needed “so the database can authentic(sic) [they] really are mutually following each other with the victim.”
It’s clear that this isn’t a “web exploit,” but a somewhat clever scam that’s designed to trick users into handing over their usernames and passwords.
Be careful when being presented with such emails. Phishing can take a lot of different forms and they’re all dangerous.
 14 DAY TRIAL //
14 DAY TRIAL //