APWG’s Global Phishing Survey for the second half of 2013 shows some interesting trends as far as phishing is concerned. For instance, almost half of the 681 organizations whose customers have been targeted in H2 2013 have not been targeted in H1 2013.
“Phishers appear to be looking for companies that are newly popular, have vulnerable user bases, and/or are not ready to defend themselves against phishing. From the results of our latest survey, it is obvious that most any enterprise with an online presence can be a phishing target,” said Greg Aaron of Illumintel, co-author of the report.
Unsurprisingly, banking, e-commerce, money transfer, and social networking and email services have been the most targeted.
In addition to the usual targets, the list also includes AirBNB, Hertz Rent-a-Car, Home Depot, Boise State University, Alliance Islamic Bank, the National bank of Vanuatu and several Bitcoin-related services.
A total of 115,565 phishing attacks were detected in the second half of 2013. Of the 82,163 domain names used for phishing, close to 23,000 were maliciously registered. It’s worth noting that in the first half of last year, only 12,000 domain names were registered by cybercriminals for phishing.
Chinese cybercriminals are believed to be the cause of this increase.
“Malicious domain names — meaning domain names registered by phishers directly, were at an all-time high — nearly twice any prior survey,” Rod Rasmussen of IID, who has also contributed to the report, noted.
Rasmussen continued, “These domains were largely registered by Chinese phishers to attack Chinese targets but were registered in several TLDs at numerous registrars around the world, making it ever more important for registrars and registries to be on the lookout for fraudulent registration attempts.”
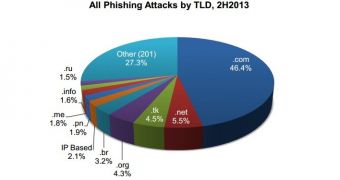
A total of 210 TDLs have been used, but most of the domain names registered by cybercriminals for phishing were on .com, .tk, .pw, .net, .info, and .cf.
As far as phishing attack uptime is concerned, APWG reports a considerable decrease. In fact, the company says that it has been close to a historic low. The average uptime was 28 hours and 43 minutes, but half of attacks were active for less than 8 hours.
The number of attacks relying on URL shorteners has increased, but that’s mainly a result of abuse at a certain provider. Close to 90% of the 999 attacks that relied on URL shortening services abused tinyURL.com.
The complete Global Phishing Survey is available on APWG’s website.
 14 DAY TRIAL //
14 DAY TRIAL //