Piyush Malik, an independent security researcher from India, has identified an Expression Language (EL) Injection vulnerability in Zong, a mobile payments provider acquired by PayPal in July 2011 for $240 million (€171 million).
EL Injection vulnerabilities were first documented in 2011 by Stefano Di Paola of Minded Security and Arshan Dabirsiaghi of Aspect Security. These are attacks that target the EL interpreter.
EL vulnerabilities can be exploited for various tasks, including code execution on the impacted server, which is exactly what Malik has found.
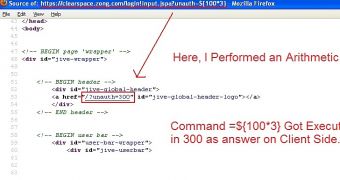
According to the expert, Zong was running an outdated variant of Clearspace (Jive Software) on a subdomain.
“Clearspace is a knowledge management tool and is integrated with Spring Framework. EL Pattern was used in Spring JSP tags which made Clearspace vulnerable to this bug,” the researcher explained in a blog post.
“There were two input forms on that application and both of those were vulnerable. One was login!input.jspa and another one was emailPasswordToken!input.jspa and the commands were executed via 2 different parameters,” he added.
It turns out that a couple of screenshots demonstrating the existence of the vulnerability were more than enough to convince PayPal. The reward given out by PayPal has not been disclosed, but it’s somewhere in the range of thousands of dollars.
Additional technical details on the Zong LE Injection vulnerability are available on Piyush Malik’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //