A security researcher encountered a threat sample identified as Zbot by five of the 52 engines available on VirusTotal.
Zbot, also known as Zeus, is a Trojan designed for data stealing purposes, focusing on confidential details such as online credentials and banking information, but it can be crafted to target other types of details as well.
Jonathan French from AppRiver caught an email carrying a payload under the form of a ZIP archive, purporting to deliver customer statements from Berkeley Futures Limited, an options broker.
This was actually part of a phishing campaign and the message came with a malicious ZIP attached that was password protected; the password was delivered in the body of the email, which should ring alarm bells because it defies the file security purpose.
Upon closer inspection, it became clear that the file had in fact been created using RAR compression; the ZIP extension was probably placed in order to confuse some scan engines or the author added it by accident.
RAR compression is rarely used by cybercriminals, mainly because the format is not supported natively on Windows, the most prevalent target, and users without a compression program installed cannot open the malicious file.
The archive analyzed by French contained two files, one of them being the executable and the other a fake invoice in PDF format.
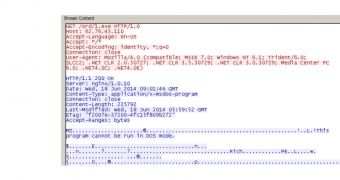
According to the researcher, the payload was a Trojan downloader that delivered the Zbot sample to the affected computer. The malware downloader itself showed that it was compiled in late May this year, and only three engines on VirusTotal detected it as a threat.
After connecting to a remote location in Russia, judging by the IP address, the downloader retrieves file “1.exe,” which is disguised with the Amazon logo for an icon. It is 220KB in size and five of the scanners on VirusTotal label it as malicious, all of them agreeing that it is a Zbot variant.
Further inspectin of the malicious file reveals that it attempts to connect to another Russian-based server, but, in this case, the connection is not established.
The case is quite weird because of the RAR archive masquerading as a ZIP, which diminishes the chances of making more victims.
Another oddity is the failure to connect to the second location, which could be the actual command and control server sending commands and receiving the information stolen from the victim. This is all for the better, though.
AppRiver, developer of email and web security solutions, says that they are “blocking this malware with over 40,000 hits so far this morning.”
 14 DAY TRIAL //
14 DAY TRIAL //