A Swiss security researcher discovered a customized variant of the infamous ZeuS which no longer uses a Domain Generation Algorithm (DGA) to determine the currently active C&C domain.
Security expert Roman Hüssy, who came across the new edition of the malware admitted that at first he thought that the malicious element is not actually ZeuS, but after further investigation he concluded that it is, just an improved version of it.
“The *new* version of ZeuS (v3?) implements a Kademlia-like P2P botnet. Similar to the Miner botnet, ZeuS is now using a “IP list” which contains IP addresses of other drones participating in the P2P botnet. An initial list of IP addresses is hardcoded in the ZeuS binary,” Hüssy revealed.
What's interesting about the improved bank account-stealing Trojan is that it only uses DGA if everything else fails. Because HTTP is only utilized to receive commands from the botnet master and for dropping the stolen data to the drop zone, BinaryURL and ConfigURL are not necessarily present, which means that it's harder to track.
So how does it work?
When it lands on a computer, it will immediately look for an active node by sending UDP packages. If such a node is found, it will reply with a list of IPs that take part in the peer-to-peer network. After getting information on the binary and config versions utilized, it will check for a recent form which allows him to connect to the node via a TCP high port to download the updated binary or the current config file. Finally, the HTTP bit steps in and the bot connects to the C&C domain listed in the configuration file.
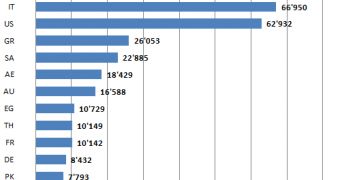
The research further shows that India currently has the most infected systems, Italy and the US closely following.
The expert advises security industry members to keep a close eye for strings such as gameover.php, gameover2.php or gameover3.php in the web proxy log, which indicate the presence of ZeuS' new variant.
Hüssy concludes that Slavik, the original creator of the malware, is still the one pulling the strings and by launching such alternatives he hopes to attract less attention from authorities while increasing his incomes.
“Slavik probably dropped this business and released the source code for public to get out of this situation. But I believe that he is still developing on ZeuS, but only custom build(s) for a small circle of customers who are able to pay a lot more money that small fishes.“
 14 DAY TRIAL //
14 DAY TRIAL //