A new email campaign has been detected to deliver Pony stealer disguised as a PDF file purporting to contain details about an overdue invoice.
The document has a double extension and is, in fact, a COM executable file that includes commands for downloading the malware from a compromised website, after running a few unpackaging procedures.
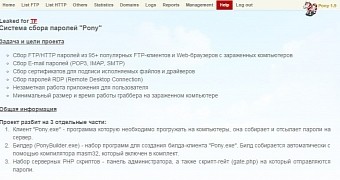
The newest variants of Pony feature capabilities for stealing crypto-currency wallets available on the infected computers but can also exfiltrate sensitive information as well as download other malware families.
Security researchers from Avast analyzed the hacked website used by cybercriminals to host the malware and found that other threat samples were being hosted. This can be done because of a backdoor specifically created for this purpose, allowing complete access.
Apart from this, the researchers noticed that the site was used to place several Pony stealer administration panels on it, along with the original installation package.
Users are advised to exercise caution when receiving unsolicited emails that try to convince them to open documents claiming to offer information about a payment.
As noted by researchers at Damballa, among other capabilities present in Pony stealer, there is decoding of passwords saved by a significant number of programs, from digital currency clients and FTP managers to web browsers and email clients.
 14 DAY TRIAL //
14 DAY TRIAL //