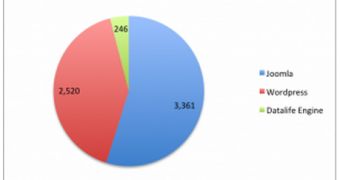
Security researchers from Arbor Networks have been monitoring a new 25,000-strong botnet that has successfully launched brute force attacks against over 6,000 Joomla, WordPress and Datalife Engine installations.
Experts say the campaign, dubbed “Fort Disco” because of a string found in the metadata field of a portable executable (PE) file, began in May 2013 and it’s still continuing to this day.
At least four variants of a piece of malware are related to this campaign. The malicious elements communicate with six command and control (C&C) servers.
The malware contains a hardcoded list of usernames and passwords. For the username, the list consists of up to five variants, usually “admin” or “administrator.”
As far as the targeted sites are concerned, experts say between 5,000 and 10,000 are targeted at a time.
When a valid username/password combination is detected, the malware sends it back to the C&C.
“It’s unclear exactly how the malware gets installed. We were able to find reference to the malware’s original filename (maykl_lyuis_bolshaya_igra_na_ponizhenie.exe) that referred to Michael Lewis’ book ‘The Big Short: Inside The Doomsday Machine’ in Russian with an executable attachment,” Arbor experts noted.
“Another filename, proxycap_crack.exe, refers to a crack for the ProxyCap program. It’s unclear if victims were enticed to run these files, and if so, if that is the only means of infection. The C&C sites did not offer additional clues as to the infection mechanism.”
Most of the targeted websites are hosted on Russian (.ru) domains, followed by .com, .ua, .net, .org, and .info domains. In most of the successful attack cases, the passwords were “admin” and “123456.”
So who is behind the Fort Disco botnet? Based on several clues, researchers believe the owner is based in a post-Soviet state, such as Russia or the Ukraine.
 14 DAY TRIAL //
14 DAY TRIAL //