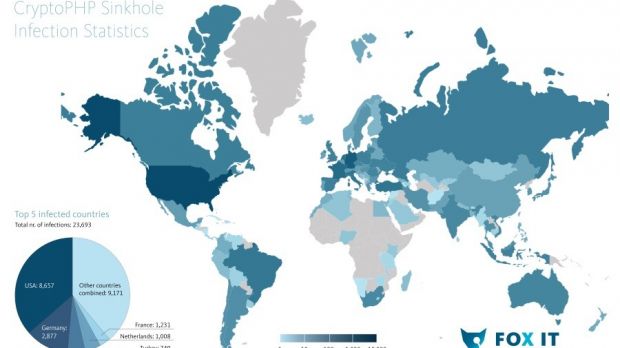
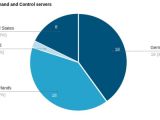
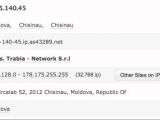
Command and control (C&C) servers used by the operators of the CryptoPHP threat for popular content management systems (CMS) WordPress, Drupal and Joomla have been sinkholed and researchers observed connections from 23.693 unique IP addresses.
Information on the scale of the CryptoPHP operation was gathered by Fox IT in cooperation with Abuse.ch, Shadowserver and Spamhaus.
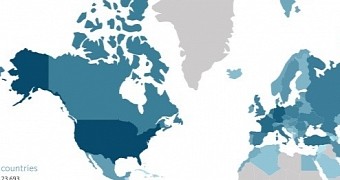
Most infections registered in the US
After sinkholing most of the active C&C servers, the researchers noticed a decrease in the amount of addresses contacting them. As such, following the initial statistics on November 22, less and less IPs initiated communication with the control domains, 16,786 being recorded on November 24.
However, researchers draw attention to the fact that the information is not particularly relevant for counting the amount of compromised websites because the affected web servers could host multiple sites; thus, malware on several websites could attempt connection to the malicious command and control server through the same IP, which makes the possible number of infected sites larger.
According to data from the researchers, most of the infections are located in the US, where 8,657 compromised addresses were recorded. Next, at a considerable distance, is Germany, with 2,877 IPs.
CryptoPHP is dynamic in use, employed for Blackhat SEO
Fox IT detected about 16 versions of CryptoPHP, the first one being spotted in September 2013. These are distributed through thousands of pirated copies of plug-ins and themes for the popular CMS software. The latest version of the threat is 1.0 and it was discovered on November 12.
Researchers say that many of the websites used to spread the threat disappeared on Sunday, only to re-emerge on Monday with a new version of the malware, and they are still active today.
Fox IT says in a report that CryptoPHP is used for Blackhat SEO, by injecting links and text into pages, but only when the visitor resembles a web crawler, which is generally used by search engines to index content.
Blackhat SEO (search engine optimization) is a technique that increases the rank of a website in a search engine through unethical means. The practice violates the search engine’s terms of service and, therefore, leads to banning the promoted website.
Public key encryption used for communication
It is believed that the actor behind this operation is located in Chisinau, the capital city of the Republic of Moldova. The information has been extracted based on a user-agent named “chishijen12,” which led to an IP address that used it since December 2013.
The list of features of the malware relies on RSA public key cryptography for the communication between the victim and the C&C, which is the reason researchers cannot compile statistics regarding the CMS software type running on a compromised web server.
If the C&C server is taken down, communication is carried out via email. Furthermore, security experts also found that the backdoor can also be controlled manually, without the need of a command and control machine.
Removing CryptoPHP
To help administrators determine whether CryptoPHP is present on their website, Fox IT created two Python scripts, available on GitHub; one is intended for detecting the presence of the threat, while the other scans for backdoor files.
Cleaning the site involves not only getting rid of the malicious scripts but also removing any extra administrator accounts and resetting the log-in credentials.
Although the routines presented by Fox IT should be enough, researchers recommend installing a clean copy of the CMS, just to make sure that attackers have no door in.
 14 DAY TRIAL //
14 DAY TRIAL //