Twitter messaging platform is an important resource for cybercriminals, and more than 20,000 accounts have been seen to be used in phishing campaigns to send out malicious links.
The scheme is simple, and generally a single compromised account is enough to spread the bad URLs and dupe unsuspecting users into providing the keys to their Twitter service on fake login pages.
More than 13,000 different addresses used in phishing links
Basically, after hijacking one account, the cybercriminal can send a message to a friend of the victim inciting them to click on a link that points to a phishing page. When accessed, the address loads a fake Twitter login page, creating the impression that the user has been signed out, for some reason.
By attempting to check the content of the URL, the potential victim tries to log back in, but all information entered in the fake fields is sent directly to the cybercriminals and the account generates a new message with a phishing link.
Security company TrendMicro has observed this phishing scheme for a period of three months, starting March 1. The report compiled from the results informs that, on peak days, crooks used more than 20,000 accounts to send links to over 13,000 distinct addresses.
22,282 compromised accounts were used on March 18, 2014 to distribute phishing links. A day later, 23,372 users delivered malicious URLs with 5,148 different addresses.
“Since June, however, Twitter has largely got on top of this and the volume of Twitter specific phishing has been significantly reduced,” Jon Oliver, senior architect at TrendLabs, says in a blog post.
Phishing on Twitter is more difficult to catch
Monitoring malicious activity on Twitter is particularly difficult for security researchers because they cannot use automated tools that are efficient for catching malware.
Honeypots, sandboxes, and web reputation instruments cannot pick the bad messages, because they are sent from one legitimate user to another and contain shortened URLs.
The researchers managed to find a way to identify the malicious tweets. Some parameters for this task would include content, embedded URLs, hashtags, and sender data (frequency included).
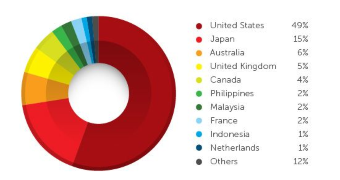
According to the report, the largest number of clicks (49%) on phishing links recorded during the three-month study came from the United States, followed at a great distance by Japan, with 15%.
Other countries falling into this trap are Australia (6%), the United Kingdom (5%), Canada (4%), Philippines, Malaysia, and France (all three accounting for 2% each), Indonesia and the Netherlands (both with 1% each).
 14 DAY TRIAL //
14 DAY TRIAL //