Since its public disclosure last week, Shellshock has been seen to be leveraged in the wild by the systems of multiple security companies, some statistics reporting more than 17,400 attacks with over 1,800 domains involved, just before the weekend.
The systems of security company Incapsula, which offers website and web application protection solutions, picked up intense activity in a period of just 24 hours late last week.
The public was informed of the Bash vulnerability dubbed Shellshock on Wednesday, September 24. Telemetry published by Incapsula on Thursday shows that malicious actors spared no time taking advantage of the flaw.
An average of 725 incidents per hour have been recorded
The number of attacks grew exponentially on Thursday night, peaking at about 2,500. By computing the results from their systems, researchers at Incapsula determined that on average, about 725 attacks occurred every hour.
These were initiated from a total of 400 unique IP addresses, and most of them had their origin in China and the United States. This is no indication that the attackers were from these countries, though.
Researchers also say that more than 57% of the incidents were performed using cURL, a utility that integrates a library and a command-line tool for transferring data through different protocols.
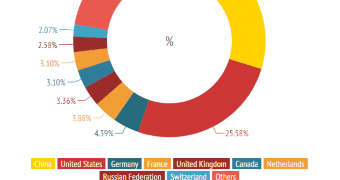
According to a graphic offering details about the geographical distribution of the IPs involved in the events, China is on the first spot, with 29.72%. The US is not too far away, as it fell in second position, with 25.58%.
Botnets used to compromise more systems
Other countries on the list are the United Kingdom, Russia, Germany, France, Canada, Netherlands, and Switzerland.
“What we are seeing here are hacker using existing botnets to create new ones: running automated scripts from compromised servers to add more hijacked machines to their ’flock’,” said Incapsula security researcher Ofer Gayer, in a company blog post on Friday.
The tools of the attackers were DDoS bots that had been assigned the new task of exploiting the Shellshock vulnerability. The researcher assumes that some of these incidents have led to a successful compromise, increasing the already large botnet army.
A series of patches for the Bash command-line interpreter for Linux and OS X systems have been launched, but developers kept finding flaws in the tool.
At the moment, the patch from Red Hat product security researcher Florian Weimer is the latest one that promises to isolate parsing code appended by an attacker to a variable function, “in almost all the important use cases we can currently think of,” Google security engineer Michal Zalewski said; he is the finder of two new remote code execution vulnerabilities that can be leveraged against systems patched with the first fix.
 14 DAY TRIAL //
14 DAY TRIAL //