An intensification of cyber attacks in Syria has been observed as security researchers find remote access Trojans (RAT) being delivered through activist websites and social networking pages relating to the political conflict in the area, to individuals seeking news or tools for ensuring private communication.
The most prevalent RATs malware operators rely on are ShadowTech, Xtreme, NjRAT, BitComet, Dark Comet and Blackshades, some of the malicious files being downloaded more than 2,000 times, according to a new report from Kaspersky researchers.
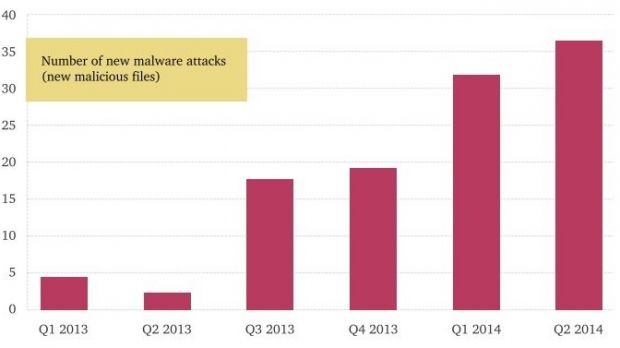
They say that the attacks did not increase only in number but also in complexity, leveraging powerful social engineering techniques that created more than 10,000 victims.
Lack of technology awareness, coupled with trust in social networking and other communication channels, is among the main factors leading to effective infection vectors.
Kaspersky tracked the methods employed by the threat actors and discovered that the malicious files allowing complete compromise of the computer were received by unsuspecting users through download links offered through Skype, Facebook posts, and YouTube videos.
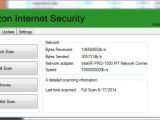
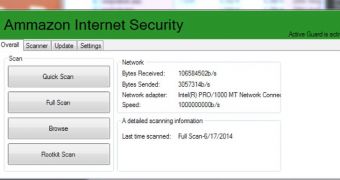
Victims are delivered links to fake programs claiming to provide encrypted communication (SSH VPN), antivirus solutions (Ammazon Internet Security) or firewalls, and fake Whatsapp and Viber applications for PC.
In plenty of cases, users are lured with documents claiming to disclose wanted activists, videos presenting victims of recent bombings or images of leaked papers from Syrian officials warning military units of chemical attacks.
Once accessed, these files deliver the malware on the computer giving the threat actor unrestricted access to the system. Keylogging, recording of audio and video, executing arbitrary programs, downloading files, exfiltrating data, remote shell and executing denial-of-service attacks are among the functions provided by the RATs.
Although cyber attacks in Syria are nothing new, the novelty in this case is that the malicious campaigns have become more organized as malware operators started to create “highly stealth and graphically-enticing applications.”
“Among the most popular RAT found in the samples subset is Dark Comet, a free remote administration tool that provides a comprehensive command set for the attackers to use in their malicious purposes,” the researchers write in the report.
In their investigation, Kaspersky managed to identify a group with a highly organized structure (dubbed the Resistant Syrian Electronic Army) broken into multiple teams in charge of specific tasks: Team Hacker and Assad Penetrations Unit (Team 1), Anonymous Syria Al Assad Unit (Team 2) and Management of Electronic Monitoring and Central Tracking Unit (Team 3).
Kaspersky predicts that, because of the rapid evolution of the cyber attacks against Syrian citizens (over 100 samples have been collected), the attackers may soon proceed to writing their own malware instead of relying on known threats.
“With enough funding and motivation they might also be able to get access to zero day vulnerabilities, which will make their attacks more effective and allow them to target more sensitive or high profile victims,” they conclude.
 14 DAY TRIAL //
14 DAY TRIAL //