Romanian grey-hat hacker Unu makes a comeback with a big bang – a critical SQL injection in Orange.fr. Exploiting the vulnerability exposes the names, e-mail addresses and plain text passwords of over 245,000 users.
The newly reborn Romanian HackersBlog has published details of an SQL injection vulnerability affecting Orange's online presence in France. Discovered and reported by the outfit's former, but most prominent member, Unu, the flaw can have devastating privacy and security consequences for a very large number of French Orange customers.
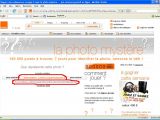
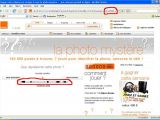
"Orange is so cool... when they share members info’s [sic.] with anyone," the Romanian hacker ironically writes, before publishing his proof, in the form of screenshots. The images reveal that the vulnerable page is on Orange's Mystery Photo portal (http://laphotomystere.orange.fr), which runs on a Debian 4.0 (Etch)-powered server with MySQL 5.0.23 on the backend.
The administrative account of the database, predictably called laphotomystere, is also named, how other than, laphotomystere. The password is not revealed in the screenshot, for obvious security reasons. In another demonstration, Unu extracts the details of the account with the number 245,000, the lucky winner being someone called Yasmine. Part of the information in the image has been blotted by the hacker in order to prevent abuse.
Gunter Ollmann, vice president of research at Damballa and, formerly, chief security strategist at IBM Internet Security Systems, notes on his blog that, "Over the years I've dealt with numerous folks working within the security teams of Orange around the world and they're generally a smart bunch of folks, so this lapse in security is rather disappointing. I can only presume that (as is so typical nowadays) this particular Web portal element was designed and developed by a third-party and didn't undergo the usual security scruitiny. [sic.]"
However, regardless of who's fault it is, this is a major security blunder, nonetheless. Even though Unu has vowed in the past never to misuse information obtained as a result of his Web-hacking endeavors, the affected Orange costumers should still proceed with changing their passwords, as someone else might have figured out how to exploit this vulnerability for less altruistic purposes.
"In the meantime, if you are an orange.fr customer and are concerned about the safety of any other online accounts you may have, I would encourage you to change your passwords on those other accounts, and of course on the orange.fr web site," Rik Ferguson, solutions architect at antivirus vendor Trend Micro, advises. "Recently published research showed that 61% of people use the same password for multiple sites, so this kind of compromise represents real risk for many people," he adds.
Of course, the passwords are not the only reason for concern, as the rest of the information such as names and e-mails can be of great value to spammers and identity thieves. The hacker notes that he informed the company's staff of the issue, but that he's yet to receive a reply from them. Meanwhile, the page seems to have been taken offline.

 14 DAY TRIAL //
14 DAY TRIAL //