An international group of highly skilled cybercriminals infiltrated the networks of up to 100 financial institutions across the globe and gained administrative control over the computers, robbing about $1 billion / €876.7 million.
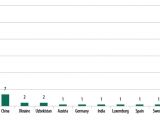
The attack is currently active and most of the victims have been identified in Russia, USA, Germany, China and Ukraine. However, there is indication that the operation is extending to regions in Asia, the Middle-East, Africa and Europe, security researchers at Kaspersky say.
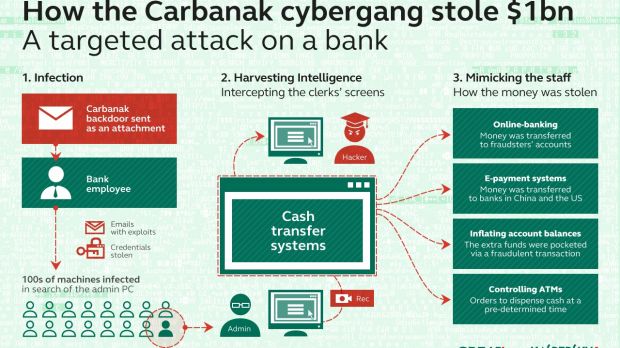
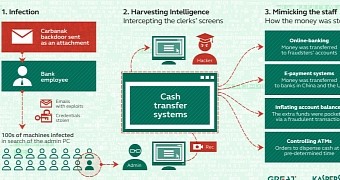
Attackers rely on spear-phishing for initial infection
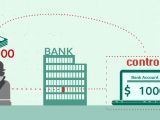
One of the methods used by the hackers to cash in after penetrating the bank’s network was to instruct ATMs (automated teller machines) to dispense money at specific times, without inserting a payment card.
Another one consisted in artificially inflating account balances of bank customers and then transferring the surplus to bank accounts of the cybercriminals in China and the US; they would also open fake accounts with a fake balance. One victim lost $10 million through this type of illegal transfers from its internal platform.
Kaspersky says that the attackers use spear-phishing to gain access to the targeted network. The emails would carry malicious attachments exploiting two vulnerabilities (CVE-2012-0158 and CVE-2013-3906) in Microsoft Office 2003, 2007 and 2010, and one in Microsoft Word (CVE-2014-1761). Additionally, they observed that Control Panel Applet (CPL) files were also leveraged in the attack.
“Once the vulnerability is successfully exploited, the shellcode decrypts and executes the backdoor known as Carbanak,” which was initially derived from the leaked source code of Carberp Trojan, the researchers say in a report. Later versions of the malware do not rely on Carberp’s code.
Reconnaissance lasted between two and four months
The goal of the attackers is to move laterally in the network in search of systems handled by administrators and compromise them. This allows them to impersonate legitimate local users that have the appropriate permissions to carry out the actions initiated by the cybercriminals.
According to the researchers, the Carbanak group spent between two to four months inside the compromised systems doing reconnaissance activity, which included keylogging and video captures of the infected admin system.
After learning how the targeted banking platform worked, they would steal the money, between $2.5 / €2.187 million and $10 / €8.753 million per heist.
In one case, a financial institution’s ATMs were emptied of $7.3 million / €6.4 million. Remote attackers would initiate the command to dispense the money from the machine while an accomplice would wait for the cash to simply pop out, with absolutely no interaction.
Out of the 100 banks attacked, Kaspersky says that at least half of them recorded financial losses.
Carbanak is just a different name for Anunak
From the samples analyzed by Kaspersky, the malware was compiled in August 2013, when it is believed Carbanak started to be tested. Infections were detected in December 2013, which indicates that actual thieving began in February-April 2014. The largest amount of infections was recorded in June 2014.
Although Carbanak is a new name on the security scene, its usage has been observed before by security experts from Fox-IT and Group-IB, who presented it as Anunak in December 2014, as this was the name given by the malware author.
Fox-IT says that the cybercriminal group has decreased its activity since early December. However, this may very well be a matter of visibility across the globe, as the reports from these two security companies and from Kaspersky share stark similarities in the modus operandi.
Moreover, the report from Group-IB focuses on victims in Russia and informed at the time that there was no evidence of successful compromise or theft from financial institutions in a different country.
 14 DAY TRIAL //
14 DAY TRIAL //