Some laptop computers from Apple are vulnerable to a major security risk that allows an attacker to overwrite the BIOS of the machine and lace it with a rootkit, thus gaining control over the computer.
Although an attack requires modifying the code that deploys the very first instructions for starting the system, no physical access is necessary. Exploiting vulnerabilities in other software such as Safari browser would be sufficient for a successful compromise.
Attack can be executed after system wakes up from sleep mode
Security researcher Pedro Vilaca discovered the vulnerability starting from the Thunderstrike flaw presented by Trammell Hudson at the Chaos Communication Congress (CCC) in 2014.
Both weaknesses touch on bypassing the security measures for accessing the Extensible Firmware Interface (EFI - the successor of BIOS firmware interface) and modifying it.
However, Hudson’s approach entails physical access to the device, while for Vilaca’s method to work the only prerequisite is to have the system freshly woken up from sleep mode.
Forcing the computer to enter sleep mode can be added as a routine in the attack; users may not view this as a reason for concern, and upon waking the system, the compromise can occur.
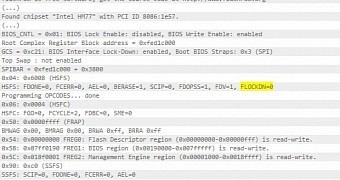
Firmware protection - disabled
The researcher explains that, for some reason, after a suspend-resume cycle, the value for the flash lockdown (FLOCKDN) protection that keeps the firmware read-only becomes 0 (zero), indicating the possibility to overwrite it with an update.
The rogue firmware code can be deployed from “userland,” a part of the operating system where code not belonging to the kernel is executed. “The flash is unlocked and now you can use flashrom to update its contents from userland, including EFI binaries,” Vilaca says.
There is little users can do to protect themselves
The severity of the issue is significant because BIOS firmware runs at a lower level than the operating system and no installed security solution can detect the malicious code.
Other solutions that would work for uncovering regular malware, such as reinstalling the operating system or replacing the hard disk are also completely inefficient when facing this type of compromise.
Vilaca says that Mac laptops released prior to mid-2014 are affected, surmising that “Apple either fixed it by accident or they know about it,” adding that this is not “something you just fix by accident, just sayin’.”
He tested the glitch on a MacBook Pro Retina, a MacBook Pro 8.2, and a MacBook Air, all of them with the latest EFI code available, and all of them tested positive.
One way to protect against this type of attack is to change the sleep mode settings of the machine and prevent it from slipping into slumber when idle for a longer time.
Vilaca offers a solution for finding out if the EFI code on a Mac machine has been compromised, although the method is suitable for advanced users. It involves dumping the contents of the BIOS chip and comparing the firmware with the one provided by Apple. Trammel Hudson provides the tools (SPI Flash Reader) necessary for this activity.
 14 DAY TRIAL //
14 DAY TRIAL //