The final version of the Cybersecurity Framework has been released. Work on the framework, which aims at helping organizations in the critical infrastructure sector, started one year ago, when US President Barack Obama signed an executive order on “Improving Critical Infrastructure Cybersecurity.”
During this year, organizations and individuals from the United States and other countries have contributed with guidelines, best practices and standards. The best ideas have been incorporated into the voluntary Cybersecurity Framework by the National Institute of Standards and Technology (NIST).
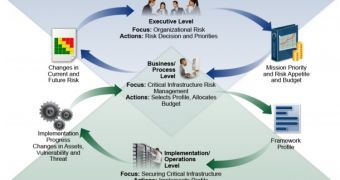
The framework provides a road map to show organizations the steps they need to take in order to secure their systems.
It has three main components, designed so that they reinforce the connection between cybersecurity and business drivers.
The first component is the core, which represents a set of activities and informative references that are common for all sectors. The cybersecurity activities are grouped into five categories: identify, protect, detect, respond and recover.
The second component is “Profiles.” This enables organizations to align their cybersecurity with business requirements, resources and risk tolerance. The profiles can be used not only to determine a company’s current posture, but also to measure progress.
The last component, called Tiers, is designed to help organizations in managing cyber risk. The tiers are numbered from 1 to 4 (1 being “partial” and 4 being “adaptive”). They’re used to describe various factors, such as the degree of rigor in risk management practices, and the integration of cybersecurity risk management into the organization’s overall risk management practices.
Critical infrastructure organizations are not forced to adopt the Cybersecurity Framework. So, in order to encourage them to do so, the DHS has established the Critical Infrastructure Cyber Community (C3) Voluntary Program to encourage its adoption.
It’s worth noting that critical infrastructure organizations from all over the world can use the Cybersecurity Framework, not just ones from the US.
 14 DAY TRIAL //
14 DAY TRIAL //