It appears that while OS X is quite robust and well made in terms of holes that can be exploited without the user's knowledge and input, it is still as vulnerable as anything else to social engineering.
The latest alarm has been raised by Alastair Houghton, who explains on his blog how the OS X authentication dialogue can lie.
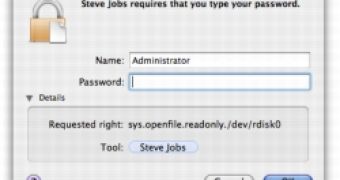
It looks like the Authentication dialogue can be made to lie about what program is requesting authorization. In the example shown in the screenshot, a program that is not called Steve Jobs has used the authentication dialogue to make it look like it is something else.
Doing this is incredibly easy and just about anyone can do it. Those thinking that close inspection will protect them are gravely mistaken, as the malicious program can also disguise the path where it is located to match that of another application.
If you were the target of such a malicious application and were actually deceived and entered your password, the program would get a handle for /dev/rdisk0, which would effectively give it access to all your data.
Unfortunately, while it is very easy for people to take advantage of this, even if Apple were to fix this, that would still leave the problem of anyone who wanted being able to replicate the exact look and functionality of the authentication dialogue and use that to acquire your password. One possible solution to this would be something secret, that you would tell the computer, and it would use to authenticate with you? just like you give it a password to let it know it is you, the system would tell you its password to let you know it is not some bogus program.
 14 DAY TRIAL //
14 DAY TRIAL //