Security researcher Nir Goldshlager has identified a serious bug in the OAuth system used by Facebook, which allowed him to gain full control of any user account, even if the victim never “allowed” any apps.
The OAuth system is used by Facebook for communication between apps and users. When users want to install an application such as Texas Holdem Poker, they’re asked to grant it permission.
The attack method is based on the URL of the OAuth dialog, which looks something like this:
app_id=YOUR_APP_ID&next=YOUR_REDIRECT_URL&
state=YOUR_STATE_VALUE&
scope=COMMA_SEPARATED_LIST_OF_PERMISSION_NAMES
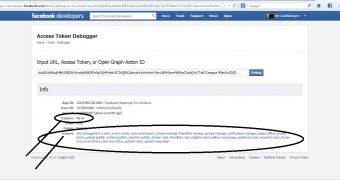
However, after some more research, Goldshlager managed to obtain the victim’s access token without the need to install an app. He did this by replacing the “app_id” parameter with the one of Facebook Messenger.
Since the access token expires only when the user changes his/her password, and since Facebook Messenger implicitly has all permissions, the expert was able to gain full access to any account.
Facebook addressed the security hole after being notified by the researcher.
The expert says he has identified additional OAuth vulnerabilities in Facebook, but he’s waiting for the company to address them before making their details public.
This is not the first time when Goldshlager identifies serious flaws in Facebook. At the beginning of January, he reported finding a vulnerability in the Secure File Transfer service used by Facebook employees, which allowed him to reset the password of any account.
Complete technical details of the OAuth hack are available on Nir Goldshlager’s blog.
Here is a proof-of-concept video of the Facebook OAuth hack:
 14 DAY TRIAL //
14 DAY TRIAL // 