Cybercriminals operating botnets have registered a slightly larger number of command and control (C&C) servers in 2014, according to a report from Spamhaus.
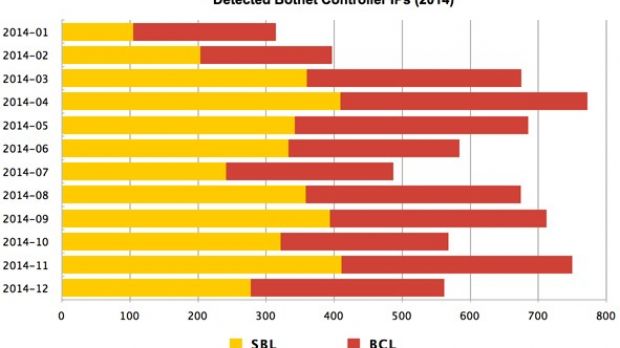
The organization detected that 7,182 IP addresses have served at some point during the year as a C&C server, the number being higher with 525 addresses compared to 2013. Translated into percentage, this accounts for a 7.88% increase.
Almost 1,200 networks hosted botnet controllers
Spamhaus is an organization that tracks down email spam and maintains lists with the IPs the unsolicited messages originate from. These lists are used with email servers and by Internet Service Providers (ISPs) to cut down spam delivered to users.
The organization also manages a Botnet Controller List (BCL), with the specific purpose of providing other entities with the means to protect their users. The BCL consists in IPv4 addresses that can be blocked without fear of affecting legitimate traffic since they point to no legitimate services.
The report published on Wednesday says that the botnet controlling addresses were dispersed across 1,183 different networks and were hosted on compromised web servers.
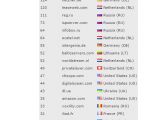
As per Spamhaus’ data, most of the C&C servers this year were located in the OVH network in France, which hosted 189 of them.
Networks in other countries are also available in a top 20 created by the organization, Russia being most present, with a total of 278 command and control servers distributed over four networks. Netherlands was a predominant country too, also with four networks, hosting 265 C&C servers.
Banking Trojans were most common type of malware
As far as malware families infecting the computers go, Spamhaus lists ZeuS banking Trojan at the top of the list, followed by Citadel. Both of them have been on the radar of both law enforcement and security researchers, who joined efforts in dismantling the networks of infected machines.
Coming in third place is Asprox malware, which is specifically designed to recruit new machines for the botnet with the same name. Its operators often rent it to cybercriminals who distribute different pieces of malware.
Other malware families included in the report from Spamhaus are Dyre (also known as Dyreza), Shylock (which has also been targeted by law enforcement operations this year), Tinba (which emerged as the smallest banking Trojan), Vawtrak (also known as Neverquest), and Geodo.
Most of these threats are banking Trojans built to target customers of specific banks across the globe; they are continually evolving, and protecting against them requires a multi-layered defense approach.
As it was expected, the prediction for 2015 regarding botnet activity is not optimistic and cybercriminals will continue to resort to infecting large amounts of computers in order to achieve their financial goals.
 14 DAY TRIAL //
14 DAY TRIAL //