Over the past months, security researchers from Kaspersky have been monitoring a cyber espionage campaign aimed mainly against South Korean think tanks.
According to experts, the operation, dubbed Kimsuky because of the “kim” names used to register drop box email accounts, appears to be launched by North Koreans.
The list of targeted organizations includes The Sejong Institute, the Korea Institute For Defense Analyses (KIDA), the Ministry of Unification and the Hyundai Merchant Marine. Eleven of the targeted companies are based in South Korea and two in China.
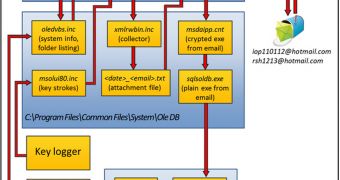
The cybercriminals infect the computers of these organizations with a piece of malware that’s capable of logging keystrokes, collecting directory listings, stealing HWP documents, remote control access and remote control download and execution.
It’s uncertain how the malware is distributed by the attackers because the campaign is very limited and highly targeted. However, experts highlight the fact that in such operations, malware is most often delivered via spear phishing emails.
So why does Kaspersky believe that North Korea might be behind the attacks?
First of all, because of the profiles of the targeted organizations. They deal with research on international affairs, they support groups for Korean unification, and they produce defense policies for the government.
“The targets almost perfectly fall into their sphere of interest,” Kaspersky's Dmitry Tarakanov noted.
While experts agree that this and the names used to register some email accounts are not conclusive evidence, there are other aspects that point to North Korea’s implication in the campaign.
Specifically, the IP addresses used by the cybercriminals. All of the ten addresses observed by Kaspersky are in ranges of China’s Jilin Province Network and the Liaoning Province Network.
However, the ISPs providing Internet access to these areas are believed to maintain lines into North Korea.
The complete paper on the Kimsuky APT is available on Kaspersky’s website.
 14 DAY TRIAL //
14 DAY TRIAL //