Tavis Ormandy and Julien Tiennes, two security specialists from Google, reported last night (August 13th) that they had discovered a critical security vulnerability in all Linux kernels (2.4 and 2.6) since 2001, for all architectures. The CVE-2009-2692 vulnerability allows regular users to get root rights on the affected system(s). For more technical users, the actual problem is a Linux kernel NULL pointer dereference due to incorrect proto_ops initializations. The vulnerability is only local.
"Tavis Ormandy and myself have recently found and investigated a Linux kernel vulnerability. It affects all 2.4 and 2.6 kernels since 2001 on all architectures. We believe this is the public vulnerability affecting the greatest number of kernel versions." - Julien Tiennes said on his blog. "The issue lies in how Linux deals with unavailable operations for some protocols. sock_sendpage and others don't check for NULL pointers before dereferencing operations in the ops structure. Instead the kernel relies on correct initialization of those proto_ops structures with stubs (such as sock_no_sendpage) instead of NULL pointers." he added.
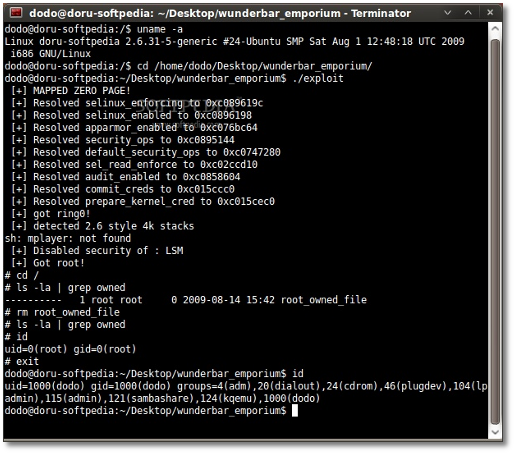
Tavis Ormandy and Julien Tiennes said that all versions of the Linux kernels 2.4 and 2.6 since year 2001 were affected by this newly discovered security vulnerability. We at the Softpedia Labs ran the sample exploit on the recently released Ubuntu 9.10 (Karmic Koala) Alpha 4 operating system with Linux kernel 2.6.31-5.24, based on the official 2.6.31 RC5 branch, and found it to be vulnerable. However, it appears that the exploit will not work on recent versions of the official Linux kernel with mmap_min_addr support, when using sysctl to assign values grater than zero for vm.mmap_min_addr. Below you can see a screenshot showing the effects of running the CVE-2009-2692 exploit.
"Since it leads to the kernel executing code at NULL, the vulnerability is as trivial as it can get to exploit: an attacker can just put code in the first page that will get executed with kernel privileges." - says Julien Tiennes, Google Security Team.A patch for the CVE-2009-2692 security vulnerability is already available here.
Click here to see a list with all the affected Linux kernels!
Edit 17.08.09: Patched versions of the Linux kernel are available for download from Softpedia. See below!
Linux kernel 2.4.37.5 Linux kernel 2.6.30.5 Linux kernel 2.6.31 RC6
 14 DAY TRIAL //
14 DAY TRIAL //