The Android browser on versions of Google's operating system used by millions has been found vulnerable as far as validating objects with a different origin is concerned.
The glitch is present in the Android browser prior to version 4.4 of the mobile OS and consists in the lack of verification of the origin of JavaScript URLs, giving a potential attacker the possibility to execute JavaScript in the context of a loaded frame.
Protection against this sort of behavior is done through a browser mechanism called same-origin policy that does not allow a site to use code from a different resource than its own.
Researcher creates PoC to steal data
Independent security researcher Rafay Baloch made the discovery in a research session on Android browser and created a proof-of-concept (PoC) to demonstrate it.
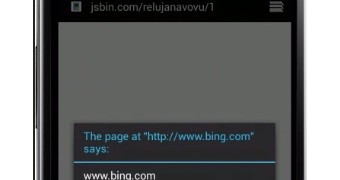
The researcher says that what the PoC shows is that “an object with data attribute, which loads up a URL from another origin.” He used www.bing.com, which was replaced with “javascript:alert(document.domain)” after it loaded in the browser.
With help from a fellow developer using the Twitter handle @filedescriptor, Baloch created proof-of-concept code that “steals data from bing.com by accessing the document.body.innerHTML property as submits that data cross origin by using a POST request, since you can send limited amount of data with GET due to browser restrictions.”
The researcher tested his code on multiple Android devices, from Sony Xperia to Nexus 4 and Samsung Galaxy S3; the PoC worked on all of them.
On Wednesday, security experts from Google released a patch for the vulnerability, which was disclosed to them on September 25; it appears that the patch is available for JellyBean users.
Google applied the fix in Chrome years ago
Baloch observed the same vulnerability in other browsers too, like Maxthon, CM Browser and Safari Browser 5.0.
Users with a faulty Android browser are advised to apply the latest patches from Google or to start using a different web navigation tool on the device, such as Chrome or Firefox.
According to Baloch, this fault was eliminated in Chrome browser years ago, but the fixes did not migrate to the Android browser.
Rafay Baloch is not at the first discovery of a same-origin bypass vulnerability in Android browser. He has recently disclosed one that has been confirmed by security researchers at TrendMicro.
It allowed a potential attacker to run universal cross-site scripting (UXSS) attacks. Just like it is the case with the latest one, the glitch affects Android browser in versions of the operating system prior to 4.4.
 14 DAY TRIAL //
14 DAY TRIAL //