Security researchers from Kaspersky have found a new piece of malware that currently targets Mac OS X users. It’s called OSX.SabPub and it’s a backdoor Trojan that’s connected to the advanced persistent threat (APT) attacks known as Luckycat.
According to experts, currently there are at least two variants of SabPub, one of them being created sometime in February 2012.
Distributed in spear-phishing attacks and hiding as Microsoft document files, it’s believed that the piece of malware is designed to target Tibetan activists.
After performing a series of tests using a decoy system, Kaspersky Lab experts have been able to determine that the bot’s command and control (C&C) server was hosted on a VPS in Freemont, United States.
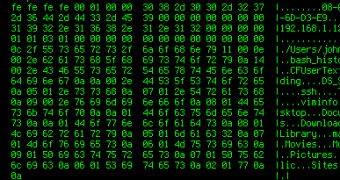
The cybercriminals that run the campaign have manually checked the “goat” system in an attempt to extract sensitive information from it.
“The attackers took over the connection and started analysing our fake victim machine. They listed the contents of the root and home folders and even stole some of the goat documents we put in there!,” Kaspersky’s Costin Raiu wrote.
While the variant of SabPub created in February leverages security holes found in Microsoft Office products, the newer version, developed in March, exploits Java vulnerabilities, similar to Flashback.
“The Java exploits appear to be pretty standard, however, they have been obfuscated using ZelixKlassMaster, a flexible and quite powerful Java obfuscator. This was obviously done in order to avoid detection from anti-malware products,” Raiu explained.
Currently, the APT that’s behind SabPub is active, researchers being confident that new variants will be seen in the upcoming days or weeks.
Unlike MaControl, another backdoor that was making the rounds in February 2012, SabPub is considered to be more effective because it managed to stay undetected for one and a half months.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile or follow me at @EduardKovacs1
 14 DAY TRIAL //
14 DAY TRIAL //