A fresh ransomware with file encryption capabilities, named Crypt0L0cker (the “o” letter is a zero) by its authors, has been discovered recently to target only machines from European and Asian countries, as well as from Australia.
The threat has a geographical restriction that prevents it from installing on systems in the United States.
Beware of suspicious emails
According to the researchers, it is not a variant of the infamous CryptoLocker whose activity was disrupted last year in Operation Tovar, but rather a variant of TorrentLocker, given the numerous similarities found (uses the same site for bitcoin purchasing instructions and the same communication method).
The malware piece reaches the victim computer via fake emails purporting to inform the recipient of traffic violations or a different type of notification from the government.
Immediately after installation, Crypt0L0cker establishes communication with the command and control (C&C) server and sends a unique identifier of the compromised computer and of the campaign.
Crypt0L0cker uses whitelist for file encryption
The ransomware then starts encrypting most of the files on the system, skipping only a bunch of them, which are defined in a hardcoded list. This actually is one of the differences that sets it apart from malware of the same kind, as ransomware authors usually build a list with the targeted extensions.
In an analysis from Bleeping Computer, the list of items that are not sentenced to encryption contains several media and text files, as well as items that are required for the well-functioning of the operating system (SYS, CMD, EXE, INI, BAT, MSI, DLL, INF or LNK).
However, the list does not include JPG, MKV, DOC, PDF and other file types that are popular with the users for storing important documents and personal multimedia data.
Volume Shadow Copies are also deleted during the encryption process, leaving no other possibility to recover the data than a backup file whose integrity has not been affected.
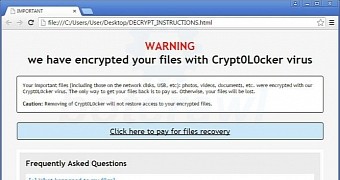
When the encryption completes, Crypt0L0cker shows the ransom note, which asks for a 2.2 bitcoin ($500 / €450) payment in exchange for the decryption key. The ransom notification comes complete with instructions for making the payment and appears each time the victim logs into Windows.
The ransomware threat does not appear to go away anytime soon, as its efficiency has been proven multiple times by infecting computers of police departments, who paid for getting the data back.
Users are advised to set up a backup plan and store copies of important files in safe places with highly restricted access to the computers used for daily tasks.
 14 DAY TRIAL //
14 DAY TRIAL //