An updated Neverquest Trojan was discovered in November, aiming particularly at users in North America, followed by Europe and Asia.
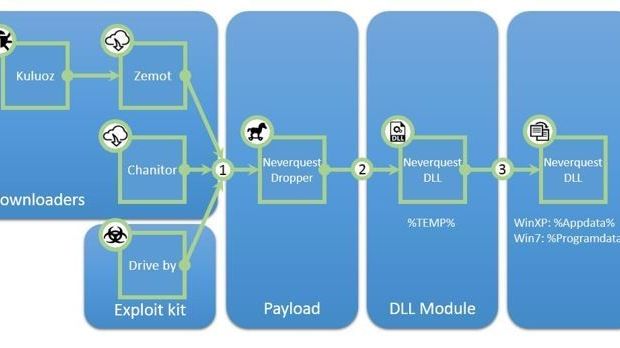
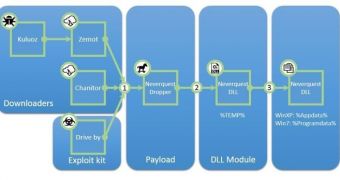
Researchers have found that the latest variant of the threat, which is also known under the name of Vawtrak, is delivered via several malware droppers, Zemot being among them.
Zemot is part of the Upatre family, which has been used on numerous occasions by the operators of the Asprox/Kuluoz botnet to funnel in additional malware on affected computers.
Finding the command and control servers is more difficult
Security researchers at IBM’s Trusteer have observed that the latest reiteration of Neverquest includes a changed installation process, and communication with the command and control (C&C) servers is now done via Tor2web proxy network.
By placing the servers in TOR, the cybercriminals protect their operation from being dismantled because connections inside the network are encrypted and randomized in order to preserve anonymity.
Trusteer threat engineer Ilya Kolmanovich notes in a blog post that apart from relying on Asprox botnet and Zemot for distribution, the new Neverquest is also delivered through exploit kits in drive-by attacks.
The modification in the infection process is completed in two steps, the first one consisting in dropping the malicious DLL payload in the %temp% folder, while the second one executes it with the “regsvr32.exe” command-line tool.
Once executed, a large number of Windows processes are injected with malicious code and the dropper is deleted from the system.
New techniques adopted to achieve persistence
Kolmanovich says that the latest strain of Neverquest relies on the “recurring key” technique to achieve persistence and immunize against removal action from antivirus products. This is done by continuously writing itself in the Windows registry.
Another technique observed by the researcher is called “watchdog” and is designed for the same purpose for its critical DLL module. These are immediately reproduced the moment they are terminated, from other injected processes.
The new sample also comes with increased capabilities, such as the possibility to record video and capture screenshots. Furthermore, a Pony module has been integrated, whose purpose is to steal credentials stored in the browser, as well as keys for email clients and FTP programs.
It appears that the latest iteration of the threat contains at the moment a list of 300 targets across the globe, not all being from the financial sector. Some of them are related to gaming, social networks and media, a clear sign that crooks are after any info that can be used to get cash.
Protecting against Neverquest depends on the security solution the user relies on. “Security products that implement a naive approach will be bypassed with every change that Neverquest implements until the new modification is studied. Until then, these products are ineffective,” Kolmanovich says.
 14 DAY TRIAL //
14 DAY TRIAL //