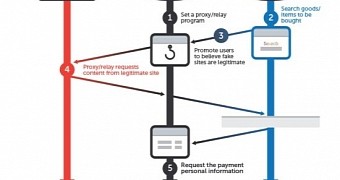
A new phishing method has been observed in Japan, where the attackers act as a proxy for a victim browsing an online shop and impersonate only the stages of a purchase that include sensitive card information.
Detecting the fraud is difficult because up to one point the user navigates the legitimate website; furthermore, after completing the fake order, the victim is also sent an email with the summary of the purchased items.
Only the checkout process is fake
The technique has been discovered by security researchers at Trend Micro, who dubbed the campaign “Operation Huyao;” they say that there is no evidence of similar cases occurring outside Japan. However, this could be only a test run before the holidays and may be adopted at a larger scale.
Running the scam is quite simple from a technical standpoint, and it appears that it could develop into a trend because the attackers could use a single domain to target multiple stores.
Relying on search engine poisoning or a wide range of lures, the victim is attracted to a website that intermediates the connection to a real online shopping location. When the visitor tries to make a purchase though, a fraudulent page is served for entering the sensitive information.
“It does not matter what device (PC/laptop/smartphone/tablet) or browser is used, as the attacker proxies all parts of the victim’s HTTP request and all parts of the legitimate server’s response,” says in a blog post Noriaki Hayashi, senior threat researcher at Trend Micro.
Attackers ask for verification password and security code
In an observed attack, the researcher noticed that the attacker would promote a fake “Add to Basket” function and the price of some products would appear with a significant discount to lure in victims.
In the first stage of the fake checkout procedure, the user is asked for details such as name, postal code, city or country, address, phone number, email address and password; the second step is to provide payment information (card issuer, number, expiration date, card holder name and the security code – CVV or CVV2).
An additional page is provided for defeating the 3D Secure feature adopted by some online merchants, specifically to protect against fraud; the mechanism consists of a password that is tied to the card, known only to the true owner.
The new phishing technique could become more prevalent in the future since it increases the efficiency of the deceit and lowers the effort of the cybercriminals.
They no longer have to replicate the entire website and rely on different domains for multiple stores; instead, duplicating the checkout process and using identifiers in the URL to intermediate the connection to separate merchants is enough to carry out the fraudulent task.
This relay phishing technique is believed to be employed by operators in China, hence the Huyao name, which means “monstrous fox” in Chinese.
 14 DAY TRIAL //
14 DAY TRIAL //