Mac security firm Intego has discovered new samples of the Flashback Trojan horse, Flashback.G, and claims to have seen evidence that numerous Mac users have been infected by this malware.
The Austin, TX software company reports that this new version of the Flashback Trojan horse infects Macs in one of three ways, depending on the user’s system configuration.
“The malware first tries to install itself using one of two Java vulnerabilities,” explains Intego. “If this is successful, users will be infected with no intervention.”
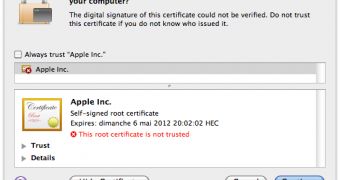
“If these vulnerabilities are not available – if the Macs have Java up to date – then it attempts a third method of installation, trying to fool users through a social engineering trick. The applet displays a self-signed certificate, claiming to be issued by Apple. Most users won’t understand what this means, and click on Continue to allow the installation to continue,” reads the company’s advisory.
Interestingly, should Flashback.G find Intego’s VirusBarrier X6 installed on the user’s system (or any other security program that can detect it), the malware stops installation, in an attempt to avoid detection.
Intego opines that "the malware writers feel it is best to avoid Macs where the malware might be detected, and focus on the many that aren’t protected."
The security firm notes that “Flashback.G injects code into web browsers and other applications that access a network, and in many cases causes them to crash.” “It installs itself in an invisible file in the /Users/Shared folder, and this file can bear many names, but with a .so extension.”
Intego then proceeds to offer some examples of users posting logs on forums about certain applications crashing, as a result of getting infected with Flashback.G.
For those who are interested in the specifics surrounding this piece of malware, the company’s full advisory can be found here.
 14 DAY TRIAL //
14 DAY TRIAL //