Security researchers warn that a new attack is capable of infecting Windows, Mac OS X and Linux systems with a new variant of the notorious Koobface worm.
The attack was spotted on social networking websites like Facebook, MySpace and Twitter, the usual hunting grounds of the Koobface gang.
It begins with users receiving a messages from their friends, who direct them to an online video. Lures like "Is it you in this video?" have been observed.
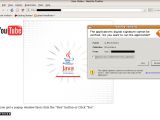
The included link leads to a fake YouTube page, which displays a video thumbnail. Clicking it launches a Java applet, that users are asked to accept.
The applet exploits a remote code execution vulnerability in outdated versions of Java and checks the visitor's operating system.
Based on this determination, the appropriate version of the Koobface worm is installed without requiring any interaction from the victim.
Koobface is the father of all social networking worms and its authors are constantly coming up with new ideas to avoid detection or to make the threat more resilient.
Once installed on a computer, the worm hijacks the social networking accounts of its owner and uses them to propagate.
Infected systems join together in a botnet and contact a command and control server, from where they receive instructions.
According to Jerome Segura, a security researcher at ParetoLogic, who analyzed the attack, the Linux Koobface version is attached to a Java applet called jnana.tsa.
The applet is dropped inside the user's home directory and stops running at computer reboot. This means that on Linux, unlike on Windows, the Koobface infections are temporary.
However, Linux computers tend to stay open much longer than Windows ones, which gives attackers enough time to use them for malicious purposes.
The attack is further limited by the fact that many consumer-oriented Linux distributions, including Ubuntu, don't come with Java installed by default.
Nevertheless, the news might be disappointing to many Linux and Mac OS X users, who seem to believe that malware doesn't work on these operating systems.
Researchers have repeatedly advised that as their market share increases, malware authors will begin viewing these platforms as attractive targets.
Update October 29: Corrected the first paragraph, which erroneously described the attack as a drive-by download. The attack requires user interaction.
Update October 30: Newly discovered information in this case suggests that the Linux infection vector might be a side effect. Read more.

 14 DAY TRIAL //
14 DAY TRIAL //