Security researchers warn that an ongoing spam campaign producing emails masquerading as IRS notifications try to pass malicious attachments as W-2 forms. The payload is delivered by specially crafted PDF documents, which are stored inside .DOC files.
The IRS is one of the most impersonated agencies in scams and other attacks. However, most of these are phishing schemes that target the taxpayer's financial information and occur in the first quarter of each year. “Despite the fact that 2009/2010 income tax year is fading away in the rearview mirror for most US citizens, cybercriminals are still [in mid-July] attempting to impersonate the IRS in order to infect your PC with malware,” security researchers from email and Web security provider AppRiver, warn.
These latest spam emails have the “From” field forged to appear as if they were sent by the “Internal Revenue Service” and come with a subject of “W-2 form update.” The W-2 form is also known as the Wage and Tax Statement and employers need to submit one for each of their employees in order to report paid wages and the corresponding withheld taxes to the Social Security Administration.
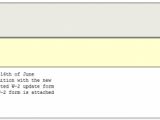
“We would like to inform you that as of the 16th of June you are late in updating your W-2 form submition [sic.] with the new updated version. Please send us your completed W-2 update form by 01/07/2010 [obvious mistake]. The updated version of the W-2 form is attached to this message,” the rogue messages read.
The attached file is called w2form.doc and opening will reveal another embedded PDF document with the instruction message (double click to view). The PDF is rigged to exploit an Adobe Reader vulnerability and install a malicious trojan on the victim's computer.
Such malicious PDFs have become a common attack vector, prompting most antivirus vendors to add signatures for most of these Adobe Reader exploits. In this case, the attackers decided to hide the document inside a .DOC in order to avoid the email being caught in rudimentary spam filters. This is a technique we've seen before with SWFs exploiting Flash Player vulnerabilities, which were embedded in Excel documents and sent via email.
All users are advised to keep their applications up to date, especially popular ones like Adobe Reader, Flash Player, Java or whatever Web browser they use, as these are also the most targeted ones. Having a capable and updated antivirus pogram installed on the computer is also a must.
You can follow the editor on Twitter @lconstantin

 14 DAY TRIAL //
14 DAY TRIAL //