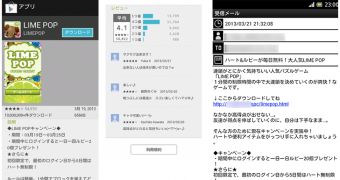
Symantec experts have been monitoring the evolution of the Android malware dubbed Enesoluty. It appears that cybercriminals are distributing the latest variant of their creation by disguising it as the popular Android game Lime Pop.
Until now, the cybercrooks have attempted to trick Japanese users into installing the malware by masking it as a battery saver, security apps or reception improvers.
Once it’s installed, the malicious element informs victims that the game is connecting to a server, after which it instructs them to check the device’s network connectivity. In the meantime, contact details from the user’s device are uploaded to a remote server.
Experts say that the main difference between this variant of Enesoluty and previous ones is mostly cosmetic.
Another thing worth mentioning is the end-user license agreement (EULA) presented to the victim. The EULA reveals that personal information might be collected from the device.
Japanese cybercriminals are well aware that such an EULA can be highly helpful in case they’re prosecuted. A few months ago, the authors of a similar application were set free because their creations clearly stipulated that information would be harvested.
 14 DAY TRIAL //
14 DAY TRIAL //