Just like all prolific pieces of malware, Backoff POS is constantly updated with new ways to steal information or to prevent detection and analysis; authors of the latest version of the malware seem to have focused on these two aspects.
The new variant of Backoff POS, the threat that affected more than 1,000 retailers in the US integrates new techniques for hiding its activity on the compromised system.
Malware drops versioning, disguises as media player
A sample of the new release was caught before October 28 by security researchers at Fortinet, who say that the changes touch on the installation process, the memory parser, and the communication with the command and control (C&C) server.
They observed that the authors dropped versioning and instead named the new string ROM; the main purpose of the tool was not changed, only some of the methods used to achieve it were.
When a financial transaction is executed at a point of sale device, the details from the card are sent in an encrypted form to the payment processor, which decrypts them in the memory of the system for a short while, to verify the transaction. Backoff is a RAM-scraping malware that can steal information residing in the memory of the computer.
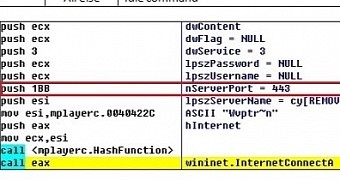
Hong Kei Chan, security researcher at Fortinet, says that in the version of Backoff POS he observed, the malware was disguised as a media player (mplayerc.exe) in the autorun registry entries that are necessary for persistency.
Generally, for increased efficiency, RAM scrapers come with a list of processes that should be ignored when collecting the card information from the memory. In the case of the new Backoff, the list does not contains the clear names of the processes, but their hashes.
Data exfiltrated securely, command strings have been removed
Chan reports that the stolen card data is now stored locally (Locale.dat), in an encrypted form, and sent at a later time to the command and control server.
“Before checking in with the command-and-control (C&C) server, ROM will first check if Locale.dat can be found. If so, it first decrypts this file and includes it in the POST request,” the researcher says in a blog post.
As far as communication with the C&C server is concerned, the latest version of Backoff uses port 443 and encrypts the traffic, hindering detection of suspicious activity.
Moreover, authors changed the names of the query strings sent to the C&C as well as the way the commands are delivered to the affected system; the command is interpreted and executed based on the modification of a single byte in the response string.
Worth noting is that the keylogging component has been discarded. Chen believes that this measure is only temporary and that the keylogger will become available in a future Backoff strain, since it is an essential feature of the malware.
The researchers have announced that another variant of the POS malware is currently under their scrutiny, and the findings of the analysis should be published as soon as the process completes.
 14 DAY TRIAL //
14 DAY TRIAL //