Since Wednesday, September 24, when the original Shellshock vulnerability for the Bash command-line interpreter was disclosed to the public, the attack rate has increased to more than 1,970 events per hour, telemetry data from a security company reveals.
Incapsula announced last week that since the bug became known to the public, in a 24-hour period, from Thursday until Friday, an average of about 725 attacks were recorded each hour, amounting to a total of more than 17,400 incidents for the entire monitored period.
Attacks increased significantly during the weekend
In an update issued this week, the company informs that incidents involving Shellshock have increased significantly, the information being extracted from their systems in a four-day period after the disclosure of the initial vulnerabilities assigned the CVE-2014-6271 and CVE-2014-7169 identifiers.
The company says that their web application firewall managed to fend off more than 217,089 exploit attempts that involved over 4,115 domains. From Sunday to Monday, Incapsula observed increased attack rates, “transitioning from short high-volume bursts into a steady stream of malicious requests.”
Malicious actors relied on different tools to conduct their attacks, from scanners used to test targeted systems for the presence of the vulnerability to DDoS (distributed denial-of-service) kits designed for injecting servers with malware.
A graph with the distribution of attack attempts shows that scanners were employed in 68.27% of the cases. Ofer Gayer of Incapsula says that only 6% of them “are likely to be used by website operators to identify the issue,” while most have been used for probing in view of a subsequent attack.
In 18.37% of the cases, attackers attempted to achieve remote shell access to compromise the servers and gain control over them.
A third major attack scenario involved DDoS malware that would add the target to a botnet used for bombarding services in order to disrupt them.
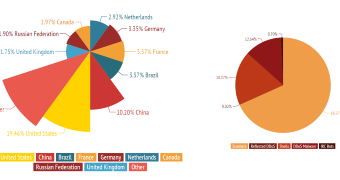
Most incidents were initiated from the United States
According to the company, Shellshock attacks originated from more than 890 IP addresses from almost every country on the globe. However, most of them (19.46%) were initiated from the United States, followed by China, accounting for 10.20% of the incidents.
Even if the point of origin of the events is located in these countries, this does not mean that the cybercriminals are also residing there; they could be anywhere on the planet.
Shellshock has received the maximum points when it comes to severity, based on the Common Vulnerability Scoring System (CVSS). It is extremely easy to exploit and it consists in assigning malicious code to a variable function run in Bash, which is executed by the shell.
 14 DAY TRIAL //
14 DAY TRIAL //