Android users are a constant target for cybercrooks, who have released a new scareware with ransomware capabilities that locks the mobile phone completely.
The fresh piece poses as a legitimate app that can be downloaded from third-party Android software repositories, and asks for administrator privileges.
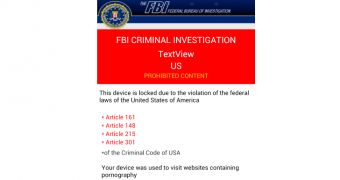
Once the elevated permissions are obtained, it automatically blocks the phone with a ransom message purporting to be from the FBI. Access to data or any function of the device is restricted, making it inoperable.
Researchers at Lookout security firm say that navigating to a different app is not possible because the malicious app, which they named ScarePakage, uses a Java TimerTask to kill any processes unrelated to the malware every ten milliseconds.
Moreover, the cybercriminals integrated a wave lock mechanism designed to instruct Android that the app needs to stay on, which prevents the phone from entering sleep mode.
The ransom message displayed on the screen purports to be from the FBI and informs that the lock has been enabled due to violation of federal laws of the United States that prohibit visiting online locations that provide pornographic content involving children, animals, as well as child abuse and spamming.
Lookout says that several hundred dollars are requested via a MoneyPak voucher in order to unlock the device. However, they also report that the app does not actually check if the voucher code works and only validates its correct length.
This could mean that the victim can provide a random code to unlock the phone, provided that they have the correct length of a MoneyPak voucher. However, this has not been confirmed by Lookout, as they did not immediately reply to our request.
[UPDATE, July 18] Following our inquiry, a response from Lookout came in, from Jeremy Linden, Senior Security Product Manager:
"Some variants of ScarePakage will uninstall themselves if you enter a random, long-enough number to satisfy the MoneyPak demand. However, this is not the case with all variants and there's always the risk that the malware authors will create future functionality to harm the user if they input incorrect data. Using preventative measures is always a better choice."
According to the security researchers, the malicious app masquerades as an Adobe Flash package, and in some cases, as an antivirus solution which even starts a scan of the device. Of course, the verification is fake, and as soon as it completes, the lock is applied to the phone.
Restarting the device does not disable the ransomware because “a boot receiver class resumes ScarePakage’s takeover of your device immediately, shutting down all other processes that the user interacts with,” says Meghan Kelly on the Lookout blog.
One precaution that could prevent having the device infected with this malicious app implies avoiding to download packages from sources outside Google Play Store.
Also, another way is to not give administrator privileges to apps that have not been verified as being delivered by trusted developers. ScarePakage does not need the phone to be rooted in order to render it inoperable; it only needs elevated privileges.
 14 DAY TRIAL //
14 DAY TRIAL //