Recent variants of the malware analyzed by security researchers show that the cybercriminals operating the Neverquest banking Trojan have focused their attack on banks in the United States and Japan.
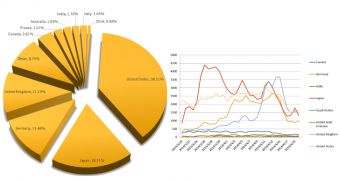
New telemetry results from Symantec inform that the largest number of infections since December 2013, have occurred in these two countries, accounting for more than half of the compromised computers.
The U.S. recorded 38.51% of the detections, while in Japan the infection accounted for 18.21%. Next in line are Germany (11.48%) and United Kingdom (11.19%).
Identified by Symantec as Snifula, in 2014 the malware recorded a spike in Japan for the month of March.
Neverquest has been around for a long time, since 2006, and the cybercriminals kept improving its malicious components.
At the moment, it is capable to log keystrokes, grab screen captures and record video, control the infected machine through remote control software, as well as steal information using man-in-the-browser (MitB) technique.
Symantec also warns that it can steal digital certificates. Exfiltrating the information is done to command and control servers operated by the threat actors.
It appears that the remote machines are also contacted for receiving configuration files customized for each target. Security researchers found different configurations for banks located in the U.S., Germany and Japan.
They analyzed this data and concluded that it can be separated into two parts, one with code for MitB attack and the other containing a set of strings that trigger monitoring when the victim navigates to a website whose URL includes a match for one of the strings.
This is most likely to collect new information about potential targets and prepare attack techniques for compromising them.
According to Symantec’s research, “There are no major differences between configurations for the US and Japan in terms of the list of strings. We can see around 400 strings related to social networking, customer relationship management, Web mail, messaging, cloud computing, storage, financial, online movie, photo sharing, and gaming services. It seems that most major online services, for both consumer and enterprise users, are covered.”
The company also says that eight Japanese banks are targeted by the latest version of Neverquest, and ten German ones; however, this figures do not compare with the more than 50 found in the configuration file for the U.S.
It appears that Japan has popped on the radar of cybercriminlas lately, as ESET details about a banking malware, identified as Win32/Aibatook, that has been distributed through compromised Japanese adult websites.
 14 DAY TRIAL //
14 DAY TRIAL //