Netflix customers are targeted lately with well-crafted phishing emails that can easily fool them at a first glance.
Cybercriminals have become more sophisticated in their nefarious activities, as they set up fraudulent web pages that are very similar to the original ones and craft email messages that look genuine.
The scheme is a classic one: crooks send email messages claiming to be from Netflix, asking for a validation of the account, for security reasons.
A link is placed at the end of the message, as an easy way for users to reach the page where the account validation information needs to be entered.
The URL actually leads to a fraudulent page that asks for all the details required by a third party to access the Netflix account.
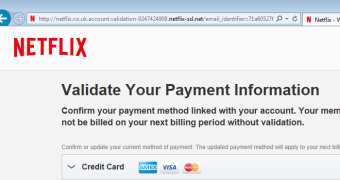
Jerome Segura of Malwarebytes analyzed such a webpage and noted that its long URL could be particularly effective on mobile devices since not all of it is displayed.
The security researcher pointed out that the web page the potential victim landed on sported better graphic elements than the samples seen regularly. The website has been reported to the registrar and hosting company and now its address is flagged as a phishing risk in all major web browsers.
Another fraud attempt involving Netflix credentials has been reported by MillerSmiles, who provided an example that could deceive the average Joe into spilling the credentials to the service.
Although both phishing pages are currently caught by the web browsers, when crooks set them up they have at least a few hours to steal the login information.
As such, users have to pay attention to the messages claiming to come from online services and asking for sensitive details; businesses would not ask for information relating to the security of the account or the login credentials via email messages.
Phishing campaigns are the cybercriminals' preferred method not just to collect login information for a particular website but also for infiltrating malware that can monitor browsing activity and gain access to banking accounts.
In a recent such incident, crooks used well-crafted emails to deliver Dyre banking Trojan to JP Morgan Chase customers.
The operators are believed to be connected to the handlers of the original Gameover Zeus botnet that was taken down at the beginning of June in a massive action involving law enforcement agencies in multiple countries and private security companies.
 14 DAY TRIAL //
14 DAY TRIAL //