Security firm Kaspersky has published the first part of a paper that focuses on a massive cyber espionage campaign in which the attackers have been using a covert surveillance tool called NetTraveler to steal sensitive data and documents, and log keystrokes.
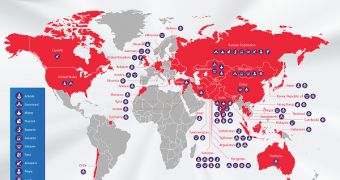
The campaign, in which advanced persistent threat (APT) actors use the malware to spy on their targets, has made over 350 high-profile victims in 40 countries.
According to Kaspersky, the earliest samples of NetTraveler are dated to 2005, but some activity might have existed since as early as 2004.
Despite the fact that this is a relatively old campaign, those who run it have no intention of putting an end to it. In fact, the largest number of samples identified by Kaspersky has been developed over the past three years.
As far as the targets are concerned, the list includes Tibetan activists, oil industry companies, universities, governments, governmental institutions, research centers, military contractors and embassies.
Most of the targets are from the diplomatic sector (32%), followed by governments, military and private organizations. The espionage group’s most recent domains of interest are energy production, nanotechnology, space exploration, nuclear power, lasers, communications and medicine.
The largest number of infections has been spotted in Mongolia, India and Russia. Other countries in which the malware has been detected include China, South Korea, Germany, the US, Canada, the UK, Austria, Japan, Iran, Pakistan, Spain and Australia.
It’s worth noting that some of the victims of the NetTraveler campaign are also victims of the Red October operation.
So who is behind the campaign? The answer probably doesn’t surprise anyone anymore.
Kaspersky says that “based on collected intelligence, we estimate the group size to about 50 individuals, most of which speak Chinese natively and have knowledge of the English language.”
The first part of the paper published by Kaspersky on the NetTraveler attacks is available here.
 14 DAY TRIAL //
14 DAY TRIAL //