Symantec experts have identified a new piece of malware that’s designed to cause some serious damage on the computers it infects. It’s called W32.Narilam and its main purpose is to modify corporate databases.
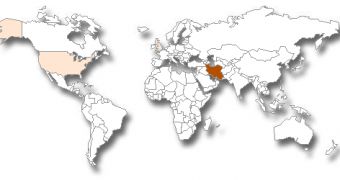
Similar to older threats such as Stuxnet and Flame, Narilam has been mostly spotted on devices located in the Middle East. However, a smaller number of infections have also been recorded in the United States and the United Kingdom.
Researchers reveal that Narilam – which is written in Delphi – copies itself to the infected machines and creates registry entries to ensure that it can step into play every time the computer is started. Similar to other worms, it’s capable of spreading via removable drives and network shares.
The most curious thing about this particular malware is that it can update Microsoft SQL databases accessible by OLEDB.
Narilam is specifically designed to target SQL databases called “alim,” “marilan” and “shahd.”
Once it finds these databases, it looks for tables and objects called “Hesabjari” – which in Arabic means “current account” –, “Holiday,” “Bank Check,” buyername,” and other similar elements related to users, orders, accounting and customer management.
After it locates these tables, the threat starts replacing certain items with random values, and even removes some tables altogether.
Interestingly, Narilam is not designed to steal any information from the affected systems. Instead, it simply causes damages to the databases of corporations.
Symantec’s Shunichi Imano highlights the fact that the threat can’t cause damage to home users because the types of databases it’s looking for are usually not found on their computers.
On the other hand, targeted organizations that don’t have backups will suffer serious losses because the information will be highly difficult to restore.
“The affected organization will likely suffer significant disruption and even financial loss while restoring the database. As the malware is aimed at sabotaging the affected database and does not make a copy of the original database first, those affected by this threat will have a long road to recovery ahead of them,” Imano said.
 14 DAY TRIAL //
14 DAY TRIAL //