Fox-IT security specialist Yonathan Klijnsma has been investigating the activities of the cybercriminal gang behind the Tritax Fake AV family.
Variants of the Fake AV, which the expert has dubbed NameChanger, have been distributed via compromised high-profile websites such as Dailymotion.com, BusinessInsider.com and even Skype advertisements.
Cybercriminals have been using threats of the Tritax family since around May 2009. Currently, there are three variants of the NameChanger Fake AV.
The malware is called NameChanger because its three versions (NameChanger.A, NameChanger.B and NameChanger.C) have used over 200 names.
Klijnsma says that NameChanger.A, which first appeared in late 2010, has used at least 52 names, including Windows Health Center, Privacy Guard 2010, Windows Troublesmaker Agent, Windows Simple Protector and Windows Remedy.
NameChanger.B appeared in May 2011 and it has utilized at least 30 names such as Windows Inspection Utility, Windows Oversight Center and Windows Repairing System.
In the case of NameChanger.C, 138 names have already been seen, including Windows PRO Scanner, Windows Protection Master, and Windows Threats Destroyer.
What’s interesting about this Fake AV is that it’s being distributed with the aid of a social engineering kit. The attackers utilize malvertising, spam and compromised websites to lure users to pages that host this social engineering kit.
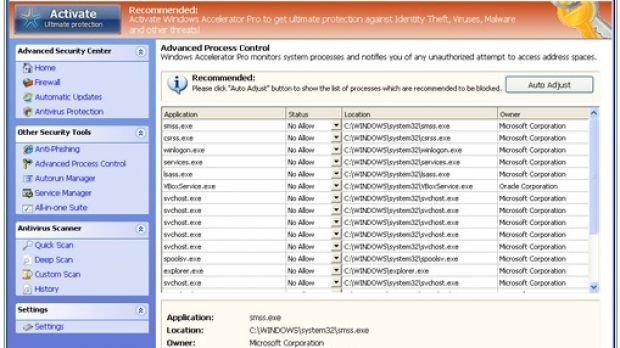
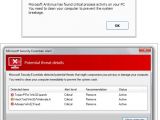
When victims land on this page, a pop-up informs them that Microsoft Antivirus has found critical process activity on their PCs. Then, a fake Microsoft Security Essentials window displays a list of threats that are allegedly infecting the computer.
When the “Clean computer” button is pressed, users are instructed to download and install an executable that actually hides the fake antivirus.
More than 200 domains have been registered between January 1 and January 25, 2014, alone. The cybercriminals have registered .pw (106), .nl (76), .pl (30) and .com domains (15). In order to save some money, the domains are registered at companies that offer a 5-day free testing period.
Additional technical details on the NameChanger Fake AV are available on the 0x3a.com blog.
 14 DAY TRIAL //
14 DAY TRIAL //