A notorious threat actor around the South China Sea region is Naikon, a highly organized advanced persistent threat (APT) group that targets victims to gather geo-political intelligence, security researchers say.
The group was brought into the spotlight by security experts at Kaspersky in April, when it clashed with another cyber-espionage actor that was dubbed Hellsing, who countered Naikon’s spear phishing attack with phishing of its own, to extract more information about the attacker and their purpose.
Attacks leverage an old vulnerability
Naikon has been in the business of cyber espionage for at least five years, the researchers say, its operations having a clear geographical focus and low maintenance requirements.
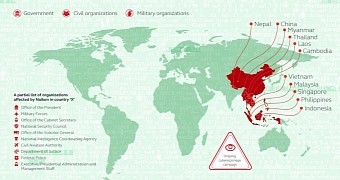
According to Kaspersky, the hackers are Chinese speakers and targeted victims are from countries like Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, Nepal, Thailand, Laos, and China.
The attack starts with a carefully crafted email that contains an exploit for the CVE-2012-0158 vulnerability affecting Office components 2003 through 2010.
The malicious file poses as a Microsoft Word document, and to remove suspicion of an attack, a decoy document is shown to the victims.
C&C operators can have 48 commands at hand
“The Naikon tool of choice generates a special, small, encrypted file which is 8,000 bytes in size, and contains platform-independent code to be injected into the browser along with configuration data. With the help of a start-up module, this whole file is injected into the browser memory and decrypts the configuration block,” Kaspersky said in a blog post on Wednesday.
According to the analysis, the main module is a remote access tool that creates an encrypted communication tunnel with the command and control (C&C) server.
A total of 48 commands have been found, allowing the attacker to add new modules for increased functionality or control the infected system via command line.
The connection between the C&C server and the victim was either direct or via a proxy, when outbound network connections were subject to monitoring. Important to note is that the C&C and proxy machines were located in the same country as the victim, making exfiltration of the data more difficult to detect.
 14 DAY TRIAL //
14 DAY TRIAL //